Atos Trustway Proteccio
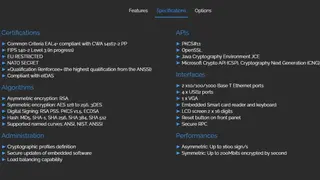
Atos Trustway Proteccio is a Hardware Security Module solution that offers a high-performance and secure environment into the company’s infrastructure so that sensitive cryptographic operations can be performed. It provides secure storage of cryptographic keys and access to protocols such as SSL/TLS and VPN. The company also offers to consult on strategic security issues related to emerging technologies.
Trustway Proteccio gives access to up to 8 virtual HSM simultaneously. Each virtual HSM is a cryptographic partition strongly separated from the others by dedicated encryption keys, users, administrators, and auditors. It offers the possibility to share the same HSM between different use cases while keeping the same security level and so getting the most of your HSM and reducing cost. The solution can be used in the banking, insurance, telecommunications, and government sectors. All in all, Yubico YubiHSM is a great service that you can consider among its alternatives.
Atos Trustway Proteccio Alternatives
#1 Thales SafeNet Payment HSM
Thales SafeNet Payment HSM is an open-source HSM that protects encryption keys used by applications in on-premises, virtual, and cloud environments. The solution makes it easier for organizations to implement secure data protection policies that are compliant with evolving regulations.
Its open API allows developers to easily integrate their applications with the HSM to store and protect keys. The API also provides flexibility for custom transaction processing, data retrieval, and statistical reporting. It’s based on key characteristics such as usage policies, range of possible values for a key, and so on.
Thales HSMs follow rigorous design requirements and pass through stringent product verification testing, followed by real-world application testing to verify the security and integrity of every device. Keys and partitions are cryptographically separated from each other, enabling Enterprises and Service Providers to leverage the same hardware for multiple tenants and appliances. All in all, Thales SafeNet Luna HSM is a great service that you can consider among its alternatives.
#2 nCipher nShield General Purpose HSM
nCipher nShield General Purpose HSM is a security solution that provides modules in order to achieve cryptographic algorithms like managing encryption and signing keys, as well as executing sensitive functions within the organization. It also includes a Trusted Platform Module.
The nCipher nShield HSM family, when combined, gives a highly scalable range of tamper-resistant hardware modules with high-speed interfaces to enable the secure cryptographic operations required to meet the demanding requirements of enterprise security applications. The latest generation of nShield HSM delivers an unmatched combination of security features for protection against physical theft and cyber-attacks combined with industry-leading performance levels.
The modules are designed for use in a wide range of applications, including banking, payments, credit card security, identity protection, and secure email. From protecting encryption keys and digital certificates to tokenizing payment transactions, you get the whole security with this all-in-one solution. It is ideal for secure storage and processing of any type of sensitive data.
The advanced architecture takes full advantage of the power offered by modern processors, supporting multiple processors in a single HSM. The modular design allows maximum flexibility making it easy to scale and adapt to changing workloads as well as future levels of performance and security. All in all, nCipher nShield General Purpose HSM is a great service that you can consider among its alternatives.
#3 AWS CloudHSM
AWS CloudHSM is a cloud-based hardware security module that provides a new and easy way for developers, system administrators, and DevOps teams to implement key management within their application architectures. When combined with services such as KMS or IAM, AWS CloudHSM provides a more secure way of generating encryption keys that are only accessible from your organization’s network perimeter.
The solution can provide key management for your application without any changes to how it communicates with your database. It encrypts data at rest and uses the data master key to encrypt database credentials, which are then stored in an encrypted column.
If you have a web application that is accessed by users from around the world and you want to ensure the security of your data and compliance with regulatory standards, this is the perfect solution for you. By using AWS CloudHSM, you can encrypt your database credentials and take advantage of our managed encryption keys service. All in all, AWS CloudHSM is a great service that you can consider among its alternatives.
#4 Utimaco SecurityServer
Utimaco SecurityServer is a Hardware Security Module that offers cryptographic key security for database servers no matter how large scale your organization is. It includes the ability to load and execute content for a task by using Smart Card technology to validate its authenticity without presenting any user interface. The system provides complete protection from unauthorized access and encryption of communication modules, thereby protecting the confidentiality and integrity of sensitive data.
A possible use case is a synchronization between two parties or systems by passing information through secure channels, including authentication and verification of both systems before passing on the data that was encrypted in one system, which then decrypts it when it reaches its destination. The use of physical hardware components provides greater security and reliability than similar software-based solutions. You can be assured that the system is operating properly since there is no reliance on onboard software to perform all functions.
Application security, data security, digital rights management, user authentication, and document protection are some examples where applications could benefit from the Utimaco SecurityServer. All in all, Utimaco SecurityServer is a great service that you can consider among its alternatives.
#5 Yubico YubiHSM
YubiHSM is cryptographic protection for servers, applications, and computing devices. It was developed by Yubico and provided advanced security service to protect servers and other configuration elements of Linux-based systems. For example, it can provide the needed key necessary for establishing a secure communication channel in TLS or SSH between the client and server. This allows enterprises to reduce costs in terms of hardware spending or cryptography services without sacrificing security.
Highlighting features of YubiHSM include Key Generation, Management, and Validation Functions. This allows all the certification authorities to be managed by a single central authority. This is also a significant step forward as it allows enterprises to leverage their key management infrastructure and applications while reducing the number of resources that they need to manage and ensuring the integrity of those keys across different platforms and applications. All in all, Yubico YubiHSM is a great service that you can consider among its alternatives.
#6 AWS Key Management Service
AWS Key Management Service allows you to manage your cryptographic keys and control accessibility while securing your Amazon Web Services and applications. The service eliminates the need to manually track which customers, permissions, regions, or other structures should use which keys. You can also use AWS CloudTrail or Amazon CloudWatch Logs to get notifications when access keys are used in an unapproved fashion. AWS KMS allows you to control access to cryptographic keys across multiple AWS services.
If a piece of information is encrypted with a key that’s stored in Amazon KMS, AWS can only decrypt the information in response to an authorized request from AWS instead of having to retrieve the key from another AWS service. This makes it easier for you to keep track of which users have which keys and helps ensure that they’re used only by authorized people.
AWS KMS makes it easy for you to move and rotate keys to manage the cryptographic keys used by your applications, grant users access to keys and control the use of those keys, generate audit logs, and encrypt data before it’s stored in Amazon S3 so that only authorized people can decrypt it. All in all, AWS Key Management Service is a great service that you can consider among its alternatives.
#7 Unbound Key Control
Unbound Key Control is a software suite that provides visibility, control, and audit of secrets across hybrid multi-cloud environments. The flexible framework enables the secure configuration management of all the enterprise’s secrets, including those belonging to cloud-native applications with microservices architecture. The solution enables organizations to manage and protect keys from a single pane of glass across any hybrid cloud and multi-site environment.
Unbound is at the core of a DevOps toolchain, delivering automated configuration management across any hybrid cloud and multi-site environment. This enables organizations to ensure the platform can be managed in production as it was in development. Minimize manual configuration changes to avoid security incidents, manage secrets across hybrid environments for agility and flexibility, and reduce complex patching cycles. All in all, Unbound Key Control is a great service that you can consider among its alternatives.
#8 Azure Dedicated HSM
Azure Dedicated HSM allows you to create and maintain keys that access and encrypt your cloud resources, apps, and solutions such as Windows Azure SQL Database. The keys used to decrypt data at rest in a virtual machine, access the physical storage of an elastic pool, and secure the data that is being processed can be generated on the Azure Dedicated HSM. Conserve IT resources by sharing information with your other cloud resources by using the same or different encryption keys for all shared resources.
Azure Dedicated HSM devices can be deployed globally across several Azure regions. They can be easily provisioned as a pair of devices and configured for high availability. Identify new threats and respond quickly with services that are informed by real-time global cybersecurity intelligence delivered at a cloud-scale. All in all, Azure Dedicated HSM is a great service that you can consider among its alternatives.
#9 Self-Defending Key Management Service (SDKMS)
Self-Defending Key Management Service (SDKMS) is a solution that is designed to enable organizations to rapidly deploy, manage, and enable secure use of cryptographic keys on-premises and in the cloud. It is designed to help organizations use the most appropriate type of key management technology while providing a single point of contact to manage keys and certificates across sites and locations.
From a security perspective, the self-defending architecture is designed to provide an optimal experience for all users by integrating many different existing technologies into a cohesive process. The SDKMS provides key sharing capabilities between the cloud and on-premise environments, which enables organizations to ensure that keys can be shared securely between these two environments.
The SDKMS acts as an arbitrator between different key management components to make sure that users can manage and use their keys in the most optimal way without having to worry about technology lock-in. The core value of the SDKMS is enabling customers to make decisions around their key management solution using a single standard.
It provides support for every Microsoft cloud service, whether it runs on-premises or in a public cloud-like Azure, as well as any third party or open source key management infrastructure. All in all, Self-Defending Key Management Service (SDKMS) is a great service that you can consider among its alternatives.