Genuity IT Management Platform
Genuity IT Management Platform is a cloud-based IT Service and Asset Management platform that automates, tracks, and reports on all aspects of your organization, IT environment, infrastructure, and assets. This simple yet powerful platform earns top marks across customer satisfaction, usability, feature set, and more. Now your IT Service, Asset, and Workforce Management teams can better collaborate, manage and report on the health of your business’ IT environment all in one place.
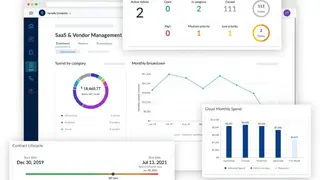
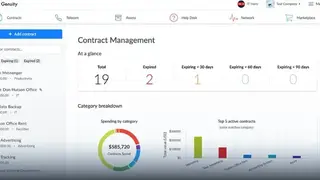
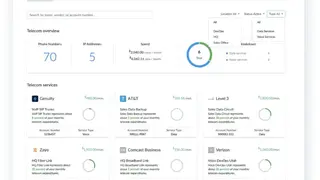
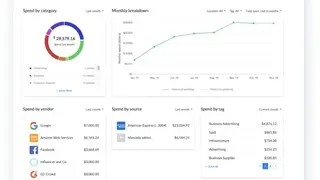
The platform includes a suite of cloud-based applications that integrate with popular accounting software and is delivered via the SaaS model. The suite includes five applications Dashboard, Service Request, Asset Manager, Contract Manager, and License Manager, that can be used individually or in conjunction with one another to efficiently manage customers’ IT assets and contracts. The dashboard is designed to give business leaders an overview of their entire organization’s IT infrastructure. It provides at-a-glance information on an organization’s network assets, contracts, service requests, and asset histories.
Genuity IT Management Platform Alternatives
#1 SailPoint Identity Platform
SailPoint Identity Platform is a Cloud Enterprise security and Identity platform that delivers a single unified solution to manage access and identity, along with privileged access and compliance. It is a powerful tool for IT departments, that need to protect what truly matters, their people, data, applications, and infrastructure. Its comprehensive policy management ensures consistent application of role-based access across the business, ensuring only authorized individuals can perform critical tasks.
In addition, it offers a hosted service that customers can use to manage social media passwords through a simple user interface without having to invest in additional hardware or software. It also allows customers to quickly manage employee passwords across multiple domains and accounts while meeting compliance requirements. Ensure you’re always protecting sensitive information according to regulatory requirements. Improve the speed and accuracy of access certifications via automated reviews and always be audit-ready. All in all, SailPoint Identity Platform is a great platform that you can consider among its alternatives.
#2 Okta Lifecycle Management

Okta Lifecycle Management combines with App Provisioning enabling customers to go from zero to hero with the reliability of enterprise-grade service and the agility of a SaaS. Businesses can provision and manage any application across any user while keeping their data secure. The platform accomplishes this through a cloud-based platform that combines single sign-on, user provisioning, and self-service password management in one console. The software allows you to manage and deploy Mobile Apps across multiple platforms such as iOS, Android, Windows Phone, Blackberry, and Web Applications such as Java, PHP, Ruby on Rails, and ColdFusion.
In addition to deploying these applications, OLM monitors them for bugs, issues, and performance problems. As cloud-based software, organizations can manage both on-premises and cloud apps, which makes Okta Lifecycle Management very suitable for multi-tenants and organizations that operate in the cloud. All in all, Okta Lifecycle Management is a great platform that you can consider among its alternatives.
#3 Saviynt Security Manager
Saviynt Security Manager is a cloud identity & access governance platform that streamlines security operations for organizations of all sizes. Executives have visibility into their data via a single pane of glass, while IT teams can easily manage and enforce access policies for data, applications, and cloud services. SSM supports delegated access and integrates seamlessly with existing network infrastructures and applications. It is designed to be easy to deploy and manage, reducing your costs by harnessing the power of the cloud.
You get a comprehensive and customizable view of all network activities and the ability to quickly and automatically respond to threats. The platform integrates with the Saviynt analytics engine, which identifies highly suspicious access patterns to help administrators implement a policy-first approach to access management. The integration between these two products delivers an end-to-end approach for providing both predictive and reactive risk mitigation capabilities
#4 N‑able Passportal

N‑able Passportal is a Password and Documentation Management platform that allows you to solve the problem of storing passwords, documentation, and other sensitive information for everyone in an office or a business. It solves the problem of having to carry your passwords and other important information with you on a daily basis by storing it all in one place. It’s easy to set up and use, even more so if you use their mobile app. It gives you the ability to synchronize all your devices and share your access with others.
A simple logon gets you in easily to your information at any time. N‑able Passportal collects all your passwords in one place, Generate secure passwords and track changes, Easily organize, find, and accesses important documents at any time, and easily collaborates with your team. With drag and drop builder, you can easily create, organize and access all the files you need, so you can spend less time searching and more time working.
#5 IBM Security Verify Governance
IBM Security Verify Governance is a cloud-based application that manages the security of software applications throughout their entire life cycle, from development to production. It brings together and extends AppScan Source’s popular capabilities with new features designed to improve governance over an organization’s software applications and automate compliance tasks. It enables organizations to automatically enforce security policies and compliance mandates across their entire enterprise. The platform consists of three components: IBM Security Verify Governance Policy Management, IBM Security Verify Governance Audit Management, and IBM Security Verify Governance Reporting.
It is offered via the IBM Cloud. You get an integrated and holistic view that simplifies management and analysis of the compliance data. The platform is designed to help organizations achieve regulatory compliance, demonstrate accountability, and improve employee productivity by automating reporting and remediation workflows. With IBM Security Verify Governance, you can get coordinated, integrated application security and governance to protect your business from the latest vulnerabilities and attacks.
#6 CoreSuite
CoreSuite is identity management and governance software that makes it easy for people to control IT and access across their enterprise. It helps IT teams implement, manage and enforce policy for username/password combinations across all devices, on-premises and in the cloud, while the identity management platform helps IT keep the user experience simple. The identity management module re-engages users with single sign-on and self-service password reset; detects risky behavior early with multi-factor authentication; assesses risk with an identity-based access review.
Access governance feature lets you set a policy once and enforce it everywhere across on-premises, cloud, and mobile apps; reduce risk with granular access controls; monitor user behavior with a single point of visibility into your environment. You can centralize security control for users and lower the cost of managing user identities by unifying user management across multiple platforms. With its innovative cloud-based architecture, CoreSuite can be deployed in minutes without a heavy footprint on the network.
#7 One Identity Manager
One Identity Manager is an Identity Management Software that enables you to manage identities, passwords, and other access controls. It’s compatible with many systems, such as Active Directory and LDAP, and it comes with customization options. The solution provides access to passwords, passwords, bank accounts, and other sensitive information that you might use while doing your daily business or personal-related stuff. Hence, it makes sure that you don’t have to go through the hassle of remembering each and every password that you have ever made for all your different accounts.
It can be used by a sole proprietor, a big company, or an organization with multiple entities. For example, you can use it for personal, business, and other business entities. The software is intricately designed to integrate seamlessly with your Office 365 and on-premises Exchange infrastructure. Key features are Session Management, Role Management, User Management, Group Management, Policy Management, Access Management, Self-Service Administration, and Provisioning.
#8 RSA Identity Governance and Lifecycle
RSA Identity Governance and Lifecycle is a security and identity management platform for enterprises of all sizes. It provides central policy, control, and compliance for strong authentication, user provisioning, and lifecycle management. The solution also features a RESTful API supporting single sign-on (SSO) and user provisioning, as well as comprehensive reporting that is compatible with the reporting requirements of multiple auditing standards for compliance. The platform helps organizations reduce costs and increase agility by automating identity governance processes, improving user productivity through self-service capabilities, and providing a single view of the user across the enterprise.
It also enables organizations to implement an effective policy-driven user lifecycle for compliant user onboarding and offboarding. Create policies and processes for onboarding, assessment, remediation, and offboarding. Monitor adherence to policies with workflow automation, multi-factor authentication, and intelligent reporting. Securely integrate with Active Directory and LDAP directories to enable bulk import of user data. Make changes via the SAML Identity Provider and easily push those changes to applications such as Microsoft Office 365. Build resilient reports with advanced analytics that integrate with Google Analytics. Send reports to a printer or PDF file.
#9 Symantec IGA

Symantec IGA is an access governance and management platform that provides comprehensive policy-based control of privileged accounts, user accounts, and apps. It is designed to strengthen the management and oversight of privileged access and the identities used to access systems and apps. Relying on a policy-driven approach, IGA helps minimize the risk of unauthorized access while simplifying the control process. The platform uses role-based policies, workflow automation, and pre-built reports and analytics to deliver comprehensive access governance for consolidated identity and access management for your enterprise.
It is engineered to help organizations to get the most out of their network access–guaranteeing compliance and elevating productivity for a new era of mobile and cloud business. IGA combines an access governance framework, identity-driven policy management, and compliance automation to deliver the ability to secure access to the right resources, on the right devices, at the right time. You get visibility into all privileged access and activity across your enterprise, Control over privileged access and activity with least-privilege administration, Automated incident detection and response (IR) from privileged activity incidents, and seamless integration with the existing security infrastructure via a single pane of glass dashboard
#10 GroupID
GroupID is an Identity and Access Management platform that securely manages user accounts, passwords, and access to applications in many areas, including Human Resources, Finance, and Office. In Standard mode, users are automatically assigned to the group with which they authenticate. In Enterprise mode, users can be assigned to multiple groups, which allows for more flexibility. The solution allows developers to implement simple APIs and other tools within their existing development environments to manage authentication and user management.
Having the ability to identify who is on your system, and provide them with the appropriate access, is crucial for any online business. With GroupID, we can make an identity for the user and monitor their access to certain information. Besides just signing into a website, it offers two-factor authentication. This adds an extra layer of security to a user’s account by using what GroupID calls a trusted agent.
#11 Micro Focus NetIQ Identity Manager
Micro Focus NetIQ Identity Manager is a powerful single-console identity management solution that ties together the systems and processes involved in day-to-day identity and access management. The software consolidates identity management processes and can eliminate redundant configuration data. The platform offers a comprehensive integration of security processes, enabling the creation of comprehensive user profiles. These profiles combine access control, enterprise federation, and information protection into a single task. Micro Focus NetIQ Identity Manager’s role-based access control allows for granular, role-based access that can be granted to individuals or groups of users.
It helps solve the complexities of identity and user administration that organizations experience as their business grows and service delivery becomes more distributed. Providing a complete solution for identity lifecycle management, Micro Focus NetIQ Identity Manager can be deployed in the cloud or on-premises, allowing organizations to choose the platform that best fits their business needs. Identity Manager also provides simplified integration with leading cloud providers and on-premises applications, such as Exchange, Domino, SharePoint, and SAP, among others, providing a flexible hybrid identity strategy giving organizations the ability to implement best-of-breed solutions to address specific business problems.
#12 SAP Access Control
SAP Access Control is a simple, cost-effective, secure authentication platform that allows site owners to manage their customer relationships and protect customer data. It helps organizations enhance the customer experience while, at the same time, meeting all compliance requirements. In addition to administrators, customers also have access to their SAP Accounts. It is a comprehensive solution to provide secure access to SAP resources based on the principle of least privilege for users and the principle of one user.
It combines identity and access management features, which are mandatory for modern SAP landscapes, with enterprise-wide encryption capabilities. The system allows each user to access only the data he/she needs or is authorized to access, and every device can be provisioned securely. Users can securely access any SAP cloud or on-premise solution, while an admin can establish and manage business policies governing resource access. Policy engine and role management are both included to drive SAP security decisions from a central point.
#13 Ivanti Identity Director

Ivanti Identity Director is a Modern Identity Governance and Administration platform that helps organizations address growing IT security threats, manage compliance and mitigate risk while enabling end-users to access apps in the cloud and on the perimeter. It instantly connects and manages identification, access, and risk policies across the enterprise. It keeps your employees, systems, and applications secure while centralizing reporting and analytics.
This single platform lets you Manage identities and access across user directories and applications, Provide self-service capabilities for employees to control their corporate access, Simplify password management for employees and administrators, and enable single sign-on (SSO) for all enterprise applications from any device or location.
In addition, with its cloud-first approach, Ivanti Identity Director can be deployed virtually and on-premises. Deployment can be orchestrated by leveraging an extension to Azure Desired State Configuration or via a simple installation wizard in silent mode. This enables IT, administrators to manage user access for cloud applications such as Office 365, no matter the deployment option.
#14 Brainwave Identity GRC
Brainwave Identity GRC is an Identity Analytics Platform for enterprises and fintech to accurately verify identities, and detect fraud and risk within days, which would have otherwise taken months, if not years. It delivers actionable insights for identity-based cyber risks and connects enterprises, consulting organizations, and service providers to integrate and collaborate for a safer digital experience. The platform fuses identity management, fraud prevention, and social intelligence in one application and provides an array of advanced analytics at an enterprise level to protect organizations against financial crime and cyber threats.
It is delivered as both services in the cloud and can be deployed as a physical appliance. Using a combination of open standards and proprietary technology, it detects anomalous activity, validates identity, and enforces security access policies, proving to be the only solution that can do that with zero false positives. You get full coverage of IT infrastructure and are able to monitor user activity at the hardware level, thus enabling regulatory and compliance bodies to leverage existing investments for monitoring employee activity.
#15 Hitachi ID Bravura
Hitachi ID Bravura is identity management and application security platform designed to help enterprises capture and leverage personal data to unlock new revenue. The platform brings together multiple security technologies to unify identity management across the enterprise cloud applications and infrastructure, creating a singular identity profile for every individual of an organization. It provides a seamless view of the true identity profile of every individual within an organization by aggregating user identities across all platforms and simplifies IT administration by integrating both on-premises and cloud-based systems.
Additionally, it enables real-time visibility into the presence of user identities across all enterprise applications with one consolidated dashboard. The Single Sign-On (SSO) feature enables secure access to protected resources across on-premises and cloud apps with one universal sign-on process. The system has been designed to simplify the management of access control and business process services from both cloud and on-premises applications and data. For example, if one were to use the system to manage access to Salesforce, it would provide capabilities such as user provisioning, password management, role-based access control, and compliance reporting.
#16 EmpowerID

EmpowerID is identity management and cloud security platform that enables organizations to protect against the growing mobile security risk threat by enabling secure mobile access while reducing the administrative overhead of BYOD deployments. Featuring a three-tiered architecture, EmpowerID’s Suite manages mobile application stores, content and data sharing, mobile device management, and employee personal productivity apps. Mvix’s Smart Phone Device Manager complements the suite by providing central management capabilities for application deployment, remote wipe, and OS updates.
It also has social login capabilities, enhanced SSO capabilities, and a new API that offers the ability to integrate EmpowerID with other applications. Its Identity Lifecycle module connects with your main HR system to inventory your entire organization and to establish both the initial and the desired compliant state. It then begins to manage the entire lifecycle of your users. All in all, EmpowerID is a great platform that you can consider among its alternatives.
#17 Immuta
Immuta is a decent and well-regarded Universal Cloud Data Access Control that provides multiple capabilities to empower operations teams, and data engineers automate data access control throughout various phases of their cloud data infrastructure with full scalability support. It is a platform that makes it easy for data teams to not only control access to data but also stay compliant and allow for secure data sharing. Using a single platform, you can automate access control for the desired data, no matter the cloud service, and on all compute infrastructure without any problems.
It is designed to integrate seamlessly into your architecture, regardless of its complexity, enabling scalable and consistent enforcement of the policy on-premise, cloud, or hybrid architecture. The capabilities include Attribute-based Access Control, Masking & Anonymization, Discovery and Classification, and Policy Enforcement and Auditing.
The platform is heavily geared towards agility and simplicity, and thanks to this, it allows data access in minutes instead of seconds. Data teams can safely share the required amount of data with as many users as necessary by masking or automatically anonymizing sensitive data. Its dynamic, policy-based access control removes the requirement for creating and managing dozens of users roles, giving stewards and data engineers the time they need to focus on other matters. Immuta supports integration with many databases, and some of these include Amazon EMR, Amazon Athena, databricks, snowflake, Amazon Redshift, Starburst, and Google Big Query.
#18 Oracle Identity Governance
Oracle Identity is an online governance solution that allows complete access to governance and comprehensive optimization of identity for actionable insights and rapid compliance. This software delivers users administration, identity intelligence, and privileged management and provides versatile actionable insight powered by rich analytics. This software comes with automated controls, risk-based analytics, and beneficial dashboards that enable rapid enterprise risk.
Cloud application service provides free account management and administration services that allow you to get complete access form shared accounts, and it also offers many abundant audit trails that ensure vast security and compliance for sensitive systems.
Oracle identity governance permits an undefined user experience and gives self catalog and drag-and-drop services, and more. It is establishing a great integrated system with bolster security and lower TCO and it lets you automatic optimization that identifies high-risk users.
#19 Frontegg
Frontegg is a web-based user management software solution that allows you to implement advanced-level and modern authentication in your application within a few minutes. It offers you features that are extremely customizable and you can change its appearance based on the image of your brand. You can use this software with any coding background but it also offers the option of the coding implementation. It offers you passionless email transactions and users are required to log in only once.
The dashboard of this software allows you to monitor every single step of implementation in real-time. Its other remarkable features are multi-tenant design, built-in authorization, admin portal, subscription awareness, PLG built-in, API supported, complete B2B as well as B2C support, and many others. If you are looking for secure authentication for your application, then Frontegg would be a perfect choice due to its personalized features.
#20 Zluri
Zluri is a simple to use software application management platform, providing you a centralized way to manage, discover, and optimize software applications. The SaaS management software is making it sure to mitigate all the potential risk by making sure the compliance and security requirement for your SaaS usage. Zluri makes sure that there is no more SaaS wastage in your IT via avoiding duplication of the application, consolidating applications with overlapping functions, and renew licenses with usability in mind.
Zluri is your premier partner when it comes to automating IT tasks, whether it be SaaS procurement, onboarding, off-boarding, and renewals notifications. The other features of this platform including complete license management, find potential inactive users, remove extra costs, eliminate compliance risks, discover unapproved applications, renewal management, contract management, user license management, reporting & insights, custom reports, and more to add.
#21 Omada Identity
Omada Identity is an advanced-level identity management software that is used to protect your organization from risks and helps you to take the action against form those risks and threats. It implements all the regulations and rules with complete compliance and policies so that you do not need to worry about the audits. You can use this software to streamline your workflow and you can easily manage your helpdesk by optimizing its operations. It allows you to implement the software on the premises of the building as well as on cloud applications.
The best feature of this software is that it permits you to generate powerful and strong credentials and login details which are difficult for intruders and hackers to breach the data. Moreover, you can give access to the employees based on their responsibility within a few seconds. If you are looking a flexible and easy-to-use software for your organization, Omada Identity would be a perfect option for you.
#22 ForgeRock Identity Management
ForgeRock Identity Management enables businesses to deliver seamless experiences for employees and customers. It empowers organizations to manage several types of identities in a single deployment, including employees, collaborators, and customers. The data model is highly extensible and allows you to change the properties of objects, attributes, and schemes, as well as the dependencies between each. The platform is fully capable of managing tens of thousands of transactions per second and, if need be, can extend support to billions of identities.
ForgeRock Identity Management is built to ensure that businesses won’t face downtime during maintenance operations, system crash, service upgrade, and network outages. This allows you to provide maximum coverage and boost customer satisfaction. The platform gives complete flexibility in picking deployment options.
By purchasing a single license, you can obtain multiple cloud environments, including development, testing, and production. It won’t charge extra fees for additional storage. It also provides DevOps tools so your IT staff won’t have to spend countless hours building their own tools. This allows developers to concentrate their efforts on fulfilling their objectives.
#23 JumpCloud
JumpCloud is a (DaaS) Directory-as-a-Service solution designed to an organization’s users to securely connect and manage their devices, files, and networks anytime, anywhere. With the help of this, you can get complete to your cloud and on-premise platforms such as Microsoft Office 365, G Suite, AWS, and Jira, etc.
It also allows you to connect with servers to share files and networks. There is also has a feature that helps you to simplify identity management as well as also enable organizations to control and manage multiple devices from a single console. Just like all the other similar solutions, it also comes with system management features to ensure that laptops and servers within the environment are under control through a complete set of security tools.
JumpCloud allows businesses to integrate it with their Wi-Fi and VPN solutions to make it more robust and secure. With its SAML 2.0 and Single Sign-On protocols, you can also be able to authorization and authentication for both web and on-premises solutions.
#24 Egnyte
Egnyte is a file sharing and content governing platform in the cloud for large-scale businesses. It offers a secure means of file-sharing services to business users. With its cloud-based services, they can easily access, share and control all of the data from a centralized platform while allowing the other connected authorized users to enjoy the same level of services.
You can still get access to your stored data as it works from any platform and device because everything is in the cloud. This is what the specialty of every cloud-based content storing and sharing platform should be. If you do not want to compromise the business agility and want to keep the information protected all the time, you need the professional services of the Egnyte.
#25 BetterCloud
Create and enforce policies for your critical SaaS application. BetterCloud is an IT management software that is known as a suite of cloud office platforms for businesses, offers automated management, intuitive data security, and critical insights.
The software allows you to leverage open API and provide a secure way to connect data seamlessly from its source and be in total control without the need for a cumbersome setup. BetterCloud has known the most comprehensive tool for cloud IT and offered all the worlds’ best features and functionality that attract more audiences around the world.
The most prominent features are auditing and discovering, customer support, fully customizable, reporting engine, monitoring, compliance, and directory management, etc. BetterCloud offers three different price plans, such as BetterCloud One Plan, BetterCloud Core Plan, and BetterCloud Enterprise Plan. Each plan has its price and core features.