Jetico BestCrypt
Jetico BestCrypt is a software that offers painless encryption to users to protect their data from physical and virtual threats. The software wipe files beyond forensics and comes with a single license all-in-one access. It protects endpoint data throughout the lifecycle through painless encryption and forensically clean files.
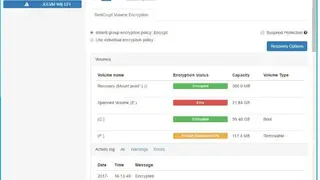
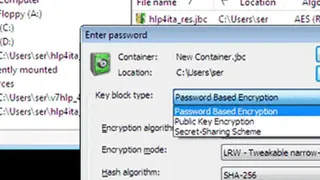
Users get volume encryption for superior whole disk encryption and container encryption for selected files. It protects users’ files from physical threats as the software is booted even before the system is in working condition to avoid any form of access to the system unless the approaching party has the password.
Users can protect their files from leaking out and keep them safe from the access of an unauthorized person. It cleans those files whose data is not needed anymore and keeps it crystal clear that even the forensics cannot access them. It comes with strong encryption for compliance, such as GDPR, HIPAA, etc.
Jetico BestCrypt Alternatives
#1 EncFSMP
EncFSMP is a reliable application that enables users to create an encrypted system and mount it either on their system or on a removable drive. The solution allows users to create a secure location in which they can store their sensitive information. It provides users an opportunity to create, mount, and edit the encrypted file system which they can easily manage when the application is running.
The solution enables users to encrypt their file systems to make them secure with a series of encryption levels. Users can choose from three different configuration options: a standard, paranoia, and the expert. Users can modify these methods according to their choice and need.
The software is easy-to-use, and users can create an encrypted file system up and running in no time. Users have to set up a master password for the main folder, which contains all other encrypted folders, and the password is not stored, which makes it safer.
#2 Encrypto
Encrypto is encryption software that helps users to protect their files with AES-256 encryption and lets users keep their files safe from unauthorized access. The software allows the users to encrypt their files before they send it to anyone from their system. Users attach a password to the files, which the other person at the receiving end can use to access it.
The solution completely secures all the files, and it ensures that only the right person gets access to it. Users can create a password hint with the password in case they forget something. Users need a password to decipher the files and get access to them.
The solution enables users to send these encrypted files via email, messages, or Dropbox or through any place; no one will access it unless they have the password. Users can save the encrypted files on their hard drive and can access them with the password.
#3 File Lock PEA
File Lock PEA is a security tool that helps users to protect their files by encrypting the individual items, or they can encrypt the entire folder. The software allows users to protect those files which they are saving locally. With its encryption, no one can access the files without the consent of the users. The software is a Java-based application that helps users to secure their files for privacy.
The solution does not require any installation, and users can store it anywhere they want and access it when they need to use it, which does not burden the system. The solution offers users to bring all their files and encrypt them all at one time.
Users only need to drag and drop the file, and the whole folder containing the files will be encrypted. The software gives users the capability to decrypt the whole folder with the files instead of separately encrypting the files.
#4 Unicode Crypter
Unicode Crypter is a lightweight software that offers services to users to manage the Unicode text with the app that provides both encryption and decryption capabilities. The solution offers a comprehensive platform to users for both basic and effective encryption and decryption tools with the Unicode format.
It comes with a two-window layout, one with the data in and the other with the data out facility. The solution allows users to input the text strings and previewing the encrypted and decrypted version of files, and Users can use the classic copy and paste tools for dropping the files in the software.
It comes with its defined and generated keys; however, users can define their keys for their use. Users can use the keys to decrypt the text after it has been encrypted. They can save the decryption and encryption keys in the system. It is a portable software, and users can take it anywhere with them.
#5 WinGPG
WinGPG is a Windows application that helps users in securing the data with a simple encryption tool. The software is simple is powerful and can keep the files secure for a long time. It helps in the protection of data and allows users to secure their files against unwanted tampering or access.
The software encrypts the documents and decrypts them easily, and allows users to secure their messaging. All of the encrypted files are zipped automatically and ready for transmission for the users. The solution enables users to sign out their documents and verify the files when they are being sent.
The software is open-source, means require no costs, and users can modify them however they want. It is free from all kinds of updates, and certifications and users can encrypt their files with pleasure. Users can make sure through the signature feature that the right person received the files.
#6 FinalCrypt
FinalCrypt is modern GUI-based software that allows users to encrypt the files and helps them in keeping away from unauthorized access. The software comes with the capability of encrypting all files in a single go, and users can select multiple files and directories to get their security. It comes with the most advanced file-encryption that is above the level of hackers, and users can secure their files for good.
The software has keys FIPS140-2 and RFC1750, which are compliant, and users can generate unlimited file sizes. It comes with an optional password that keeps the keys safe from decrypting, and the keys do not have a fixed location. The solution allows users to transfer files securely and which cannot be accessed by anyone unless they have the password. It comes with a simple interface that enables users to encrypt their files and to keep them safe all the time.
#7 KodeFile
KodeFile is an efficient tool that allows users to encrypt any photo, video, document, or other files with few clicks. The solution helps users in dealing with the encryption keys, and it generates and stores a unique key for every file that is encrypted by the software.
Users can share the secret keys with their people and can decrypt the files. The solution helps users with the hardest part of the encryption process, and that is generating the keys. Apart from encrypting and decrypting the files, it creates, stores, and shares the keys for users.
Users can generate keys for every single file, or they can create one for all the files. The solution ensures that no keys get exposed or leaked to unauthorized parties and ensures that users can trust the software. It allows users to encrypt anything and defend it against hackers, viruses, and ransomware.
#8 DCrypt
DCrypt is a Delphi-based application that allows users to encrypt and decrypt their files anytime in seconds. The solution enables users to place their files and create a container link in which they can move anywhere they need. It is installer free, which makes it accessible to users all the time, and they can anywhere encrypt or decrypt the files.
The interface comes with a simple single window that allows users to view all the options available to them. Users can write the hexadecimal code at one part of the screen and can encrypt it on the other side of the screen.
Users can assign a couple of keys and turns to apply the encryption code in seconds without writing it again. Users can set up a password to access the files, which they can use to decrypt the files. It is a lightweight tool that does not burden the system, and users can easily use it for encryption purposes.
#9 SecurStick
SecurStick is a free portable application that enables users to carry their encrypted files on a USB drive. Users can encrypt and hide files on the USB drives, and they can keep all of their files stored anywhere under complete encryption. It allows users to create a safe zone for their files no matter which system they are using.
The protected area created by this software allows users to unload their files, use them, or transfer them and clear the area after work. Users can set up a password, which they would require whenever they access the protected documents.
The protected area does not allow the users to access the files unless they give the password. All the files, after getting encrypted, are stored in a hidden folder on the target drive, and their names are encrypted along with the whole file. It is a user-friendly software and comes with a simple interface for quick encryption of files.