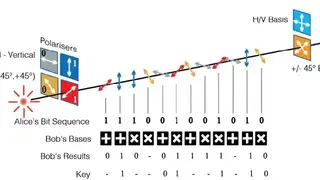
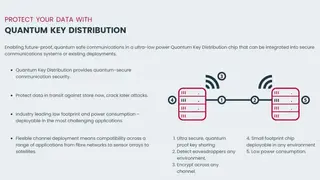
KETS Quantum Key Distribution
KETS Quantum Key Distribution service is a utility that allows future-proof, quantum-safe communications at ultra-low power in a low-cost Quantum Key Distribution chip. With the ability to be integrated into secure communications systems or existing deployments, KETS becomes an essential tool for security-conscious organizations and gives them peace of mind when it comes to the future of data protection and long-term security.
KETS Quantum Key Distribution is designed to replace existing key distribution technologies such as public-key cryptography and symmetric encryption through quantum mechanics. The system can securely distribute cryptographic keys used for high-level network communications at the highest levels of performance, safety, and reliability. It can be integrated into existing key management systems such as secure server networks and ruggedized mobile data collection units or traditional radio devices. All in all, KETS Quantum Key Distribution is a great tool that you can consider among its alternatives.
KETS Quantum Key Distribution Alternatives
#1 PGP Everywhere
PGP Everywhere is an app for iOS to generate 4096 bit RSA key pairs right on your device and then share them as text, a key server, or to your computer via USB. Under the hood, PGP Everywhere generates 2048 bit keys by default. These are automatically upgraded to 4096 bits when PGPFolks or another application that supports it contacts the server.
The interface is intentionally simple in order not to intimidate newcomers who have never seen a closed-source encryption tool before. The app offers a full range of crypto functionality from your phone. Moreover, you can share your keys, import new ones, change the keyboard layout for multiple languages without any hassle.
The app comes with email attachment decryption while importing the decryption keys from a text file. Face ID and Touch ID support is also there to eliminate the hassle of putting password and making the operation easier every time you use the app. All in all, PGP Everywhere is a great tool that you can consider among its alternatives.
#2 AxCrypt Premium
AxCrypt Premium is a file encryption utility that allows you to encrypt your files with the AES-256 bit algorithm. It does not have any limitations for files or file size. It can encrypt any file size and will not slow down the file opening process. Decrypting files is easy, with just two mouse clicks; you will not need to type in any password. You can create a ZIP or 7z archives that contain encrypted files or single files that are stored in the cloud servers like a Google Drive account.
You can also share your encrypted online documents with other AxCrypt users; this way, you do not need to exchange passwords or secret keys. You can send encrypted documents via email, and there is no need to attach the decryption key as well. All in all, AxCrypt Premium is a great tool that you can consider among its alternatives.
#3 Quantum Numbers Corp QRNG
Quantum Numbers Corp QRNG is a revolutionary way of generating random numbers, using quantum mechanics instead of the old analog technique. It offers an unbeatable level of security at any scale thus, can secure mobile and internet transactions, IoT communication, M2M connections, networking equipment, and cloud-based applications. The technology can be applied to data transmission with high-speed RFID tags and tags with Internet access by embedding it in Bluetooth Low Energy devices or Near Field Communications readers.
The QRNG is based on the principles of quantum physics and has been provided with a very low-level implementation that takes advantage of all the features of the underlying system. It uses both analog and digital processing to provide true random numbers for use in cryptographic algorithms. All in all, Quantum Numbers Corp QRNG is a great tool that you can consider among its alternatives.
#4 Eset DESlock
Eset DESlock is an enterprise-grade encryption service designed for the protection of organizations of all sizes. It has been engineered to be easy to use, manage and most importantly, comply with today’s complex security requirements. With its highly capable access control system, it is capable of managing network access and centrally managing it through Active Directory for ease of administration and flexibility with any number of domains.
Access to protected data can be restricted in accordance with multiple access policies subject to user and group rights. The solution also supports granular role-based access control and user session logging. Eset DESlock is designed to support corporate compliance with government regulations such as PCI DSS, HIPAA, SOX, and many more.
Data that goes into or out of the organization can be encrypted and integrated with existing IT infrastructure such as email servers, web gateways, and file servers. Using the comprehensive audit functionality, organizations can track where and how these systems are used, which helps meet critical compliance requirements. All in all, Eset DESlock is a great tool that you can consider among its alternatives.
#5 Homomorphic encryption
Homomorphic encryption by IBM allows you to perform computations on its encrypted data without first decrypting it. This means that both the information and the computation remain secure, even while computation is being performed on it, storing its result yet still concealed inside an encrypted container. For example, you can conduct business where your clients’ private information is kept safe and secure.
The solution securely processes sensitive data without compromising its confidentiality or integrity. Data can be encrypted before running calculations on them, so no one but the person encrypting the data has access to either the data itself or its scrambled result.
The key to homomorphic encryption is the use of algebraic operations, so instead of applying encryption after the fact, it’s applied before at the programming level. The most common homomorphic encryption applications are in processing financial transactions or breaking very large codes using existing computers or dedicated hardware. All in all, Homomorphic encryption is a great tool that you can consider among its alternatives.
#6 IBM Guardium Data Protection
IBM Guardium Data Protection is a security platform that achieves smart data protection with visibility automation and scalability. There are three main features which require this platform to work as top renowned data security platform these three pillars include, scalable innovations, seeing with insight, and automatic with purpose.
It gives you the right tools and resources, and they migrate different types of threats and attacks from your data, and it provides strategic technology initiative for moving the data to the cloud and create origin points that are encrypted and secure.
The main functions of IBM Guardium Data Protection include automatically discovering the classify sensitive data, identify the data address, get limitation recommendation, monitor access, and protect data, simplify security, compliance reporting, encrypt data across environment, get a business perspective on the used context filter inside, analytical reporting, and much more.
Every process is done in real-time and in a safe environment. It gives you robust certified encryption tokenization and key management solution. The module on the user end is easy to navigate, and all the instructions are played out in a perfect form so you can easily interact with the whole platform.
The data security and risk analysis give you a wide variety of tools and give you support over every aspect and the data recovery. The classification of quality assessment of IBM Guardium Data Protection can give you a sophisticated reporting format.
#7 BlackBerry Workspaces
BlackBerry Workspaces is the secure and private collaboration and content storage service offered by BlackBerry. This cloud-based content storage, sharing, and real-time collaboration platform allow businesses and enterprises to share files and data across the entire working environment securely. The one-liner of the popularity of BlackBerry Workspaces is again one: its file-level security system while uploading and sharing.
Its synchronization system lets its users access their stored files from any device and platform such as desktop PC, tablet, smartphone, and even its official website. It provides businessmen to equip their entire working environment and get the features of secured and synchronized files on multiple devices.
#8 Dropbox Business
Dropbox Business is a simplifying business service being offered by one of the leading cloud storage service providers, Dropbox. It is one of the best file sharing and cloud storage platforms for enterprises. It also contains some of the storage features of Dropbox and letting the business users effortlessly and robustly share, synchronize and collaborate on the common files securely.
Overall functions and services of Dropbox Business are divided into storage, file access, security, and team management. It contains all those elements that the business users need, like storage to make a backup of all files, making it a central hub for team content and advanced security and sharing controls. Each team member will get enough space to make the backup of the important files without worrying about the size of the file at all.
#9 SecureDocs
SecureDocs is a File Sharing software solution intended to provide a safe place for sorting, securing, and sharing sensitive files and documents. The software helps businesses and organizations to share documents both with internal and external parties. It can also be used for different purposes, including audits, businesses assignment and valuations, and other similar events requiring a secure location. Also, this cloud-hosted platform can be utilized as a highly secured repository for all the important documents and records. It is widely used to manage and secure business documents, especially those containing different kinds of sensitive content.
SecureDocs also make it easy for users to collaborate with external parties without worrying about control and security. Compared to all the other similar platforms, it is quietly powerful and offers an extremely user-friendly interface that makes its implementation painless. Its drag and drop feature helps in speeding up data and folder uploads. There is also a feature that allows businesses to create new roles with specific access permissions to different data rooms and functionalities. It also includes core features such as unlimited data storage, one-click archiving, ongoing upgrades, customizable permissions document watermarking, customizable click through NDA, etc.
#10 Egnyte
Egnyte is a file sharing and content governing platform in the cloud for large-scale businesses. It offers a secure means of file-sharing services to business users. With its cloud-based services, they can easily access, share and control all of the data from a centralized platform while allowing the other connected authorized users to enjoy the same level of services.
You can still get access to your stored data as it works from any platform and device because everything is in the cloud. This is what the specialty of every cloud-based content storing and sharing platform should be. If you do not want to compromise the business agility and want to keep the information protected all the time, you need the professional services of the Egnyte.