Malwares.com
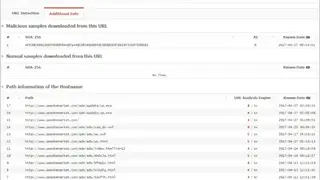
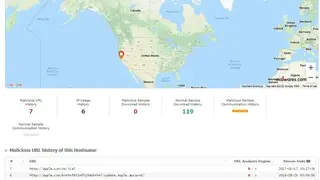
Malwares.com is a web-based malicious codes detection tool that offers a whole database system to enable users to collect and share the newest malicious codes in real-time. And also collect, create, analyze and distribute the knowledge of malicious codes. This kind of intelligence sharing system can help enterprises to monitor the latest malicious codes in the market and take action before the outbreak of malicious code and prevent the risk from spreading.
The system can conduct automatic analysis based on advanced pattern matching algorithms and security monitoring technology low false-positive rate. The knowledge of malicious codes collected by the system can help users to get the latest information about this kind of threat, including its name, path, effects, and possible countermeasures. The system also provides advanced statistics on collection data, allowing users to know the situation of malicious codes at any time.
Malwares.com Alternatives
#1 URLscan.io
URLscan.io is a website security scanner to quickly check suspicious URLs for viruses, trojans, keyloggers, spyware, and other malware prior to visiting them. It fetches the homepage of the URL and performs a series of security checks without installing any software on your computer. Based on the results, the tool will recommend whether or not it is safe to visit.
This site tests the suspected URLs from their appearance, behavior, and content point of view. If you enter a URL, the scanner will scan that URL and show a list of all the vulnerabilities. In some cases, it will also provide you with a link to a detailed report of that vulnerability. URLscan.io is powered by different anti-malware engines and checks the downloaded files against millions of malware signatures.
#2 Joe Sandbox
Joe Sandbox is an AI-based Deep Malware Analysis tool that leverages sandboxing techniques to catch malware and advanced threats that are undetected by traditional antivirus solutions. As the lines blur between malicious intent and legitimate, the tool provides visibility into a corporation’s digital footprint like never before. In addition to offering a graphical user interface that allows highly skilled users to create custom automated analyses, Joe Sandbox also provides a Sandbox API that enables programmatic access to all its features.
These include Custom algorithms and heuristics, Extensive malware behavioral analysis, Aggressive memory scanning, Decompiler technology, Malicious URL detection, and much more. Being a cross-platform tool, it can work on Windows 7, 8, 10, Mac OS, Android, iOS, and Linux. All in all, Joe Sandbox is a great tool that you can consider among its alternatives.
#3 AbuseIPDB
AbuseIPDB is an online database that helps Internet users to check if the IP they are using is blacklisted in any security systems worldwide. Users can search through the database of reported IPs, which may have been used for malicious purposes like hacking, spamming, botnet control, etc. The database contains data from various blacklists and real-time black lists.
It’s very useful for people who are about to register for any Online service or create an email address and want to check if their address is already used. Moreover, you can also report any other IP due to some malicious, fraud, or spamming activity, which will update the database and help others identify.
#4 MalShare
MalShare is a public malware repository providing access to malware samples that have been reported by users. It is created with the intent of helping security companies, virus researchers and the general public by providing malware samples in an easy to use and accessible format. It provides users with the ability to upload and download malware samples, as well as collaborative features to help with incident response and malware research.
The interface is simple with a search bar and recently reported samples. Source, file type, date and time of addition, SHA256 Hash, and Yara Hits are the information that you can see in every file. All in all, it’s a great tool for finding hidden threats that are typically scattered through public file sharing sites.
#5 VxStream Sandbox
VxStream Sandbox, now named Hybrid Analysis, is a complete malware analysis solution that allows security professionals to identify and respond to advanced threats. It provides a safe environment designed to execute malicious files on any Windows machine without affecting the host system. In order to best understand and detect malware, you can run it in a controlled, isolated environment that won’t infect your host system.
VxStream Sandbox allows you to do just that without requiring you to have your own hardware. This gives you the ability to run any malicious file with ease, Analyze suspicious files in a highly flexible sandbox, Receive immediate alerts for malicious behavior, easily review results in an intuitive web interface, etc.
#6 VMRay Analyzer Platform
VMRay Analyzer Platform is an internet security threat analysis and detection solution used by the world’s leading organizations to protect against 0-day attacks, data breaches, monitoring of network traffic, endpoint activity, and advanced persistent threats. The scalable solution combines machine learning and patented smart sandbox technology to detect attacks that evaded legacy antivirus products. This new advanced platform is designed to provide organizations with a detailed view of cyber threats and anomalies in real-time at a massive scale, up to hundreds of gigabits per second.
It combines mature security threat detection algorithms with flexible and powerful data mining capabilities powered by a top-of-the-line visualization engine. It enables security practitioners to detect and analyze security threats, isolate affected systems, and quantify the impact of a breach in real-time. VMRay Analyzer was designed from the ground up to be fast, lightweight, and incredibly adaptable. It achieves this by using carefully crafted data structures that allow the detection algorithms to run extremely fast while using minimal memory.
#7 Buster Sandbox Analyzer
Buster Sandbox Analyzer is a process behaviour change analysis and malware activity tool that allows you to monitor a portfolio of applications and generate alerts upon detection of process anomalies or unwanted behaviour. The tool addresses the growing problem of targeted attacks against the enterprise. It is designed to be used with any major antivirus software to complement its existing capabilities.
It can be used by cyber security teams for malware analysis and by malware analysts for malware reverse engineering and research. Buster Sandbox Analyzer can analyze Windows executable files, documents, PDF, Zip and self-extracting archive files. The integration with VirusTotal makes it easy to upload any suspicious file and submit it for further analysis.
#8 Triage
Triage is an easy-to-use and reliable cybersecurity analysis sandbox that allows anyone to investigate the behavior of malware. Its intuitive interface allows analysts and developers to create experiments, allowing anyone to investigate malware in the cloud without any technical knowledge or prior experience with Malware Analysis. The cross-platform support lets you use it on Windows, Android, macOS, and Linux. It will intercept your file or network activity and run it in a virtual environment so that you can see if your suspicions are correct or not.
Triage’s malware analysis sandbox is used to analyze suspicious files and documents, from potential malware to documents with embedded malicious macros. Malware can be uploaded from a local file or from URLs. It contains a multitude of tricks and techniques for extracting and reconstructing as much information about a file as possible.
#9 CyberGordon
CyberGorod is an online reputation ecosystem that protects the business, professionals, and consumers from cyber-criminals and their vulnerable IP addresses and domains. It offers a unique system of scoring and improving the reputation of websites by using the Internet users’ feedback. It is used by large and small companies to get reports about potential sites to block them and prevent a data breach. It provides users with comprehensive cyber-related background and present-day behaviours of the individual, which is built using information from public sources, social media networks, forums and blogs.
It scans and searches across 80+ data sources, including social media, business listings, web archives, deep/dark web, mobile apps and more to help identify cyber threats. The algorithm ranks account based on the combined weight of all reported information. The process delivers an actionable report for you to use for more informed decision making about your accounts and prevention against unwanted cyber infringements.
#10 VirSCAN
VirSCAN is an online multi-engine virus scanner designed to detect and remove malware in shared files. Rather than using a single anti-virus engine that may miss some threats, the tool leverages the power of multiple anti-virus engines, so your files are scanned for threats multiple times. In addition, VirSCAN offers multiple scanning options and a file repair option that repairs malware code and cleans infected files. It’s fast and can be used without installing anything.
Just upload your files or folders from your PC and check if they are infected by a virus. You can scan files up to 20MB per file, and once the scan is over, you will get the results with all detected threats, if any. Another great feature is that it also provides a description of viruses found that might be helpful in determining whether the file is infected or not. Moreover, VirSCAN automatically updates virus definitions within minutes of a new virus being discovered.
#11 Quttera
Quttera is an online Malware Scanner that lets you scan your website and gives you a detailed report on the security risks that affect it and the impact they can have on your business. When you run a website, the most important thing is to protect the sensitive data you keep on it. However, most cyber-attacks come from websites themselves and not from complex software vulnerabilities or server issues. Quttera analyzes websites and ensures they are free of malware, spyware, phishing, and online scams.
Its proprietary technology is based on constant and thorough analysis of domain name reputation and its analysis of website and files’ behavior captured in real-time. Moreover, it also proactively detects advanced threats that have never been seen before without generating false positives. This is only possible through unique, patented technology that analyzes and learns from every threat that you encounter.
#12 MetaDefender
MetaDefender is advanced threat prevention and detection tool that uses machine learning to identify and stop advanced cyber threats automatically. It combines the speed and simplicity of a cloud solution with intelligence and behavioral analytics. This new generation security solution has no false positives, no tuning, and is supported by real-time intelligence from the Dark Web. By applying a forensic analysis to each threat, this innovative technology empowers organizations to proactively protect themselves from sophisticated cyber-attacks.
An organization using MetaDefender can instantly detect, investigate and stop advanced cyber threats before it’s too late. It provides deep visibility into what’s happening on the network and across websites. Through the company’s proprietary Dynamic Behavior Analysis technology, the tool is able to detect and block phishing attacks, malware, and other malicious web content, including ransomware and zero-day threats. All in all, MetaDefender is a great solution that you can consider among its alternatives.
#13 FAME Automates Malware Evaluation
FAME Automates Malware Evaluation is a system that automates the evaluation and detection of suspected malware samples for cyber security professionals. It helps security companies to speed up the otherwise painfully long process of analyzing the behavior of malicious programs. This easy-to-use tool will make it possible to assess the nature of ransomware samples, as well as test their susceptibility to the various available defenses.
One of the most important tasks for any cyber security analyst or researcher is to make sure that the analysis tools they use are accurate enough to provide an accurate assessment of the malware sample. This is especially important when the code which is being analyzed can cause critical damage to a computer or network. FAME updates the definitions and scans every time a new sample is uploaded to the database. All in all, it’s a great open source virus scanner that you can consider among its alternatives.
#14 Any.Run
Any.Run is an online malware sandbox and a memory debugging tool that emulates the behavior of the real world, using the same techniques that malware uses in the wild. It allows researchers to easily analyze the behavior of malicious code and avoid breaking their own virtual machine when experimenting with real malware. The tool takes care of all the dirty work to create a deterministic and reproducible environment for research purposes.
This tool is not limited to just reverse engineering; it offers a set of actions that can be directly used in a malware analysis environment, such as modules, anti-debugging tricks, anti-VM techniques, and more. These actions can be used to perform dynamic and static analyses on malicious executables. The tool also offers a powerful API and can be integrated into any existing analysis workflow. This makes it very convenient to deploy and use on all computers, with no installation required.
#15 Malwr
Malwr is an online malware analysis and research platform designed to aid malware researchers in their daily work. It’s also an online malware analysis sandbox that emulates the functionality of common Anti-Virus products in an easy-to-use manner. It analyzes the sample using a variety of advanced machine learning algorithms, which include behavioral analysis and a wide array of other features. The user can review the findings of Malwr to determine whether the sample is malicious or not.
Additional features include file integrity monitoring and memory forensics. Users may monitor a host file by uploading a file or providing its location. If an attempt at modification of the file is detected, then the tool will generate an alert. Memory forensics analysis enables users to retrieve memory snapshots from their system and examine it for malicious activity.
#16 Cuckoo Sandbox
Cuckoo Sandbox is a software checking program that makes the users of Windows operating systems able to test the health of new software in advance before installing it on the computer. Unlike creating the virtual environment permanently, its way of working is a little different from those programs that create the virtual environment in the system.
Cuckoo Sandbox is an open-source automated and modular malware analysis system for Windows, Mac, and Linux operating systems. The web and cloud-based version of Cuckoo Sandbox for software testing is also available now. It enables the users to generate an isolated Windows guest environment to run safely any new application or software.
Due to its open-source feature, the users can investigate its internals and can modify it at your will. Every activity, which is recorded in its virtual environment, is generated from different types of reports like JSON report, HTML report, and HPFeeds interface.
Via this reporting feature, you can effectively understand the incident, respond to it, and protect yourself for the future. Cuckoo Sandbox is the best way to checking the internal status of those programs that are important to be installed and that are looking suspicious as well.
#17 Sandboxie
Sandboxie is a freemium application isolation and checking program that allows the developers and programmers to check for their program’s internal health and overall status. The software is designed for those who want to test their new software and are conscious about their credibility.
There are many isolation programs that allow you to test new software safely without actually or permanently installing them on a local or mapped drive. Sandboxie is that kind of program that allows the new application and software to run on your system without installation in the local or mapped drive via its isolated operating environment.
The main area of working is spread over the system of preventing unwanted changes from happening to personal programs/apps/data. Secure the web browser from viruses and other kinds of threats, run the favorite program and attach in the email, data protection system, and in last, the application testing system of Sandboxie.
#18 Hopedot VOS
Hopedot VOS is advanced and professional software that enables you to create an entirely new virtual environment similar to Windows operating systems on your system. After that, you can install and run new applications or software as you do on Windows operating systems.
It also provides personal privacy for the Internet, and all your user accounts data will be impossible to access by any third party. In short, you can perform those entire tasks that you play on your real Windows operating systems.
Apart from using it as a security for your system, you can also encrypt your applications, files, or other data into one single file. It also allows you to save your Hopedot VOS account where all your stuff is safe with Hopedot VOS.
For the information of the readers, Hopedot VOS has been discontinued, but still, the existing versions of Hopedot VOS can be used. This version can be used for performing the functions of a virtual environment, checking the health of the new software before installing them in the system.
As it is already mentioned that the developers have discontinued the software, so the support for the advanced level of issues is no more the part of the Hopedot VOS. However, it can be used for the testing of old software and programs.
#19 Shadow Defender
Shadow Defender is an advanced PC protection program that makes the users of Windows able to protect the real environment and prevent it from making unwanted changes without permission. It is a form of creating a fake or virtual environment in the system, just like the real operating environment in the system.
This virtual environment will now make the users able to protect their PC or laptop from being attacked by malicious threats or unwanted changes. It will run the system in the shape of Shadow Mode that will be a fake environment just like a real environment of the system.
All changes will be made on it instead of happening on the real one. Shadow Defender is a commercial tool designed to protect the laptop and PC from any unwanted changes. The Shadow Mode of this software will automatically control the installation of new programs and the changes that will be introduced by the new program in the system.
After installation, if you noticed any malicious activities, then you can restore the system to its original state by performing a reboot, and it looks as if nothing happened. Moreover, if you want to save any file or folder permanently on the real local or mapped drive, then you can also do the same.
#20 BufferZone
BufferZone is the name of the endpoint security system that makes the large enterprises able to keep their internal IT environment safe and secure. It is a security program that is designed to keep the IT system protect from zero-day exploits, phishing scams, and those other unwanted threats. It also created for those threats which try to make an insecure environment during the installation of any new program.
Today BufferZone is being used as the alternative of most of the leading virtual environment creators and protection providers. It isolates the threats and malfunctioning at the initial stage and provides a secure installation of software at endpoints.
The solution is useful for the business environment as business officials and staff have to deal with the usages of the Internet and removable media in their routine work. What is hidden in the new software we cannot check without installing it and installing that new software can result in threats to the system.
That’s why there comes the need for a program that automatically detects any virtual threat or virus in the software and provides secure software at the endpoint. In the case of getting back, the past state of the system, the users of BufferZone can get back it with few clicks.
#21 GeSWall
GeSWall is the name of the advanced level of intrusion prevention system that itself is easy to use and non-intrusive system. The solution ensures the safe use of the internet and provides a secure internet environment.
GeSWall will make you able to select between recommended and damaging. It is a way to keep the online environment safe and secure for you. The software is not about securing the surfing only; it will protect the web, online chatting, sharing, and almost each and everything safe and secure for you. GeSWall is a commercial and easy to use software that enables the users to surf the web, email, chat safely, transferring files regardless of threats posted on the Internet.
It is similar to antivirus, anti-spyware, and firewall that blocks unknown threats automatically and keep the original environment of your computer secure. It also keeps an eye on those viruses which are missed by sometimes by the antivirus software.
Use this software and protect your system against keyloggers, rootkits, backdoors, confidential file disclosure, targeted instructions, and malicious software infection. The main highlighted features of GeSWall have prevented all kinds of keyloggers, easy to use, no configuration required, and automatically prevent targeted intrusions.
#22 BitBox
BitBox is a free virtual environment creator for Windows and Linux. It is used for secure and comfortable web browsing. Today almost everyone uses the internet to complete a variety of tasks such as to send and receive messages, share docs, and much more. But the internet world is not secure a different kinds of threats stole your information and receive any threats or malfunctions programs from the Internet.
Here comes with a solution that helps you deliver a virtual environment that provides us secure browsing. So, via this tool, you can protect your system against any malware and data leakage. Whatever browser you are using, it will come in the shadow of BitBox that why it is also known as a ‘browser in the box.’
The way of working of BitBox is very straightforward and easy that starts from the creation of a virtual environment just like the real environment. After that, the users will be able to search securely. Never confuse the word safe browsing with those internet security providers.
The way of internet security providers is entirely different from the BitBox. BitBox is capable of creating the virtual environment in the system, but the internet security programs are not capable of this. BitBox also protects the system against data leakage and malware but by creating a virtual environment in the computer first.
#23 SHADE Sandbox
SHADE Sandbox is a security enhancement tool for the Windows operating systems. It is said to be the replacement of the antivirus and protection tools for the Windows operating systems because of being based on the security features of the antivirus programs.
However, at the same time, the software is very different from the antivirus because the way of working and protection systems of SHADE Sandbox is very different from the antivirus based program. The concept behind the operation is based on the concept of virtualization that keeps the system clean from malware and other kinds of security issues.
SHADE Sandbox will create a fenced-off safe area in the system. After that, all of them working will be operated through this area. It is similar to the creation of a virtual or fake environment on the PC, just like the real environment.
Now the running of any software or any internet activity will happen through this fake environment. In that’s the way the users of PC and laptop can ensure the protection of their system by filtering them first through the highly controlled environment created by the SHADE Sandbox. It is the way of working of SHADE Sandbox that could be more efficient as compared to most of the competitors of the SHADE Sandbox.
#24 iCore Virtual Account
iCore Virtual Account that was previously known as the iCore Computer 3-in-1 is a virtualization technology-based program to sandbox. The software is a comparatively new program in the world of sandboxing but is doing well because of possessing the state of the art protection technologies.
iCore Virtual Account is a program that will significantly reduce the threats attached to the installation of the new plan or change the configuration of the system. The working style of iCore Virtual Account is much similar to that of other sandboxing programs.
When, for the first time, you will use it automatically generate an isolated environment, and after that, you will be able to run any program securely and safely. The great advantage of iCore Virtual Account will be gain by the users during the installation of a new program or perform any online activities.
In both cases, iCore Virtual Account will provide you the additional level of security layers that it will add to the system. After these, every kind of change and configuration either because of online activities or offline activities will bind to the virtual account created by the iCore Virtual Account. The users can, in the end, even select for retaining or delete the virtual account subject to their requirements.
#25 Evalaze
Evalaze is a virtualization-based application that allows the users to install any new program. It seems to be suspicious in a fake environment instead of enabling it first to install in the real environment of the real operating systems. The software is mainly designed for those developers who are required to deal with many programs. It can be harmful to their computer because of the chances of containing dangerous and malicious elements.
Evalaze will generate a virtual assistant for you in the system that will make you able to try the installation on the virtual account instead of direct installation. Among a lot of features of virtualization and the features of Evalaze are that it supports the multiple identical apps to be run in parallel with the same system.
This system of Evalaze makes the users able to run even different versions of any programs. The main advantage of using Evalaze is that the users will not be required any more to deal with those non-virtualized apps that can be firmly anchored to the system. By using Evalaze, you will get flexibility and choices for selection whether to keep the newly tested apps or discard the changes introduced by them.
#26 Cameyo
Cameyo is a program for testing the new application or software without even installing it in the system. It is a multipurpose software program that is available for Windows and Linux operating systems.
The main highlighted advantages of using this software are the testing of any software without installing it in the system. With this, you can quickly discover the features of the program, keep the system secure by investing in the fake or virtual environment, and many others.
It is mainly designed for those programmers who are required to deal with many solutions that can be harmful. Cameyo is the name of an entire application virtualization system that is available in the shape of an independent, standalone file. Cameyo is an entirely portable application used. The users can even copy the Cameyo and can execute it in any other system.
The best about Cameyo is that it provides its virtualization and security features for both online and offline activities. In a case of offline activities, the features of Cameyo were a packaging program as a virtual program in the system, edit. They optimized the virtual application, stream the programs as the real one, and check the code of the program via open-source package editor of Cameyo. Just like offline, the online features of Cameyo are meant to deal with online activities.
#27 VMware ThinApp
Sometimes installing any new program or software in the system can be harmful. VMware ThinApp (Formerly known as Thinstall) is based on the technology of virtualization and sandbox that allow the users to accelerate the app deployment and simplified the process of migration of data.
The five essential functions that are performed by the VMware ThinApp are OS migrations, desktop security, application isolation, application mobility, and server consolidation. A real programmer can understand the importance of all these advantages in a single application.
VMware ThinApp is the best program for application isolation because it is capable of creating the virtual assistant in the system and making the application the part of that virtual environment.
In this case, the users of VMware ThinApp can make sure that the newly installed programs will never conflict with the real environment of the operating systems. VMware ThinApp is the name of security that makes it possible for the users to examine any program without even installing it in the system in the real term.
#28 Software Virtualization Solution
Are you looking for an application that provides you the system of creating a fake environment or virtual environment against the real environment? Here is the best option for you called Virtualization Solution. It is free for personal use and allows the users to try the new software, tool quickly, and even the FPS game without also polluting the system.
It will be undoubtedly hard for you after installing the desired program, and you will realize that it is not the one you were looking for. Now you are required to delete the entire setup or every file in the registry.
Instead of going through such a complicated and hectic process, there is a program that will make you able to install the new program in the virtual environment.
In that’s way, you will be able to get an in-depth analysis of your new program. In a case of not liking, that will be able to uninstall it entirely without even disturbing the real environment of your OS. In a matter of finding that program or game perfect, you can transfer its installed setup from a virtual environment to the real environment of your operating system.
A real developer understands the need for virtualization to create a sandboxing environment in the actual system. Use the Software Virtualization Solution and enjoy the benefits of virtualization and sandboxing.
#29 Comodo Virtual Desktop
Comodo Virtual Desktop is a sandboxed OS and virtualization system operated by the Comodo that is popularly known as providing the Chromium-based web browsers. It has its way of making the system of its users keep and secure.
Unlike other sandbox OS and programs that are based on the technology of virtualization, Comodo Virtual Desktop has its independent state of the art protection technology. This technology makes users able to keep the real environment of their system safe and secure for both online and offline activities.
From simple to advanced levels of tasks, Comodo Virtual Desktop is capable of dealing with all and providing in-depth security solutions for all. When for the first time, you will use the Comodo Virtual Desktop, it will create the fake operating system based environment system. It also makes you able to carry on your activities via this fake environment instead of the real environment.
The main advantage is that the application running in the Comodo Virtual Desktop environment or the browsing that you will perform will never leave the record of cookies or history. It makes it possible for the existence of a secure environment for all online and offline activities. From online banking and shopping to testing of new programs and applications, Comodo Virtual Desktop is perfect for dealing with all.
#30 Deep Freeze
Deep Freeze or Faronics Deep Freeze is a software application available to use on Microsoft Windows and Mac operating systems. The software allows administrators to protect the core OS and configuration files on the workstation or server by restoring a computer to the default configuration; each time the computer is restarted. It is also known as a Reboot to Restore Software.
Deep Freeze is a perfect choice for various PC problems, and it can avoid the associated problems of malware, ransomware, and different kinds of accidental changes by users. This comprehensive software is best for several problems that plague computers, such as malicious software activity, accidental system misconfiguration, and lots of others.
Primarily, the software works by eliminating workstation damage and downtime by making computer configurations almost indestructible. Even if the system is infected by ransom war, the software can restore your PC to the way. Before the attack, it stopped all the severe threats that much similar software can’t deal with. Deep Freeze also has a range of powerful tools that save your PC from all kinds of threads.
#31 Mbox
Mbox is based on the technology of sandbox and primarily deployed for configuration or carry on those activities on the system that are suspicious. And if you need configuration or need the troubleshooting help and want to bring back your system to the earliest stage to discard all those new changes. Then Mbox will be surely a great help for you.
It will run the system in the shape of the sandbox that will be a fake environment in the system, just like the real environment of the system. All changes will be made on it instead of happening on the real one. Mbox is a protection tool designed to protect the laptop and PC from any extra adjustments.
The sandbox mode of this software will automatically control the installation of new programs and the changes that will be introduced by the new program in the system. After installation, if you noticed any malicious activities, then you can restore the system to its original state by performing a reboot, and it looks as if nothing happened. Moreover, if you want to save any file or folder permanently on the real local or mapped drive, then you can also do the same.
#32 Toolwiz TimeFreeze
Toolwiz TimeFreeze is a system restore program based on the technology of virtualization and makes the users able to discard any unwanted changes that become part of the system. Commercial or premium software is much time secure as compared to all the other free software.
Free applications and programs can be more harmful to the system because these contain more viruses and malware as compared to the premium one. When you install these errors and malware containing applications in your system, these will change the setting of your system.
There is a way to deal securely with this issue, and that is the Toolwiz TimeFreeze that allows the users first to create a fake environment in the system and then install the software. In a case of any issue with the newly established program, the users will be able to roll automatically back to the earlier position because of the Toolwiz TimeFreeze.
Toolwiz TimeFreeze is a straightforward and efficient manner that will keep your system more safe and secure as compared to the other system protection and antivirus based programs. Use the Toolwiz TimeFreeze and get the technology of virtualization to deal with new changes before introducing them into the system.
#33 Enigma Virtual Box
Enigma Virtual Box is an advanced level of system protection system that is based on the system of sandboxing and virtualization. After installing, the users will no more be required to install any antivirus or system protection program. Because Enigma Virtual Box is capable of protecting the system against all kinds of unwanted changes, either these are coming via the online world or happening offline activities.
The way of working of the Enigma Virtual Box is entirely different from most of the sandboxing and virtualization programs. It makes the apps files and registry files able to be consolidated in a single executable file without even loss of efficiency and without a virtualized file having to be extracted to the hard disk drives.
Enigma Virtual Box is free to use application whose support is available for the x64 and x86 binaries. Enigma Virtual Box makes it possible for the developers to virtualize any kinds of files, objects, digital media files, dynamic libraries, or anything else. Even though Enigma Virtual Box provides a new level of virtualization to the users, it can’t be said as a recommended program for virtualization because of little reservation on the security of the system.
#34 Enigma Protector
Enigma Protector is designed by the developers of Enigma Virtual Box and a more advanced and secure mode of virtualization as compared to the Enigma Virtual Box. It is a software licensing, software protection, and software virtualization system based on the technologies of sandboxing and virtualization.
The software is said to be the highly advanced and professional system for executable file licensing and protection. Enigma Protecto mainly designed for the comprehensive protection of the executable files. The three main areas of functioning of Enigma Protector is file protection, licensing system, and virtual box.
First, it is vital to discuss the virtual box system of Enigma Protector because it is being mentioned because of its virtualization system. The virtual box system is based on the virtualization technology that makes the users able to combine all files used by their application into a single module without loss of efficiency.
The file protection system of Enigma Protector makes the users able to protect all kinds of executable files and the real environment of the system from being modified, hacked, and disassembly. Then there is the licensing system of Enigma Protector that is designed for verification purposes.
#35 Microsoft Application Virtualization
Microsoft Application Virtualization (Microsoft App-V) is software that is called the Microsoft App-V. It is the virtualization system by Microsoft that makes the users able to test the new programs in the Windows operating systems without even really installing then directly on the PC.
Microsoft Application Virtualization makes it easier for the IT experts to deploy across a fleet of devices by allowing access to virtualized applications to any authorized PC client.
The area of functioning of Microsoft Application Virtualization can be categorized into the category of virtualizing, manage, and restore. In addition to providing the virtualization system to the users, Microsoft Application Virtualization provides centralizes the installed programs in a central place as well.
Microsoft Application Virtualization is particularly designed for those developers who are required to deal with several programs, and that can be harmful.
The best about Microsoft Application Virtualization is that it provides its virtualization and security features for both online and offline activities. Microsoft Application Virtualization is the best way to test the new programs without even installing them in the system, and that’s why ensuring the security of the system against unwanted changes.
#36 Spoon
Spoon is a program for testing any software and application without even installing it on the computer. The way of working is a little different as compared to the normal sandbox and virtualization technology-based programs. Spoon also provides the solution of testing any new application and software without even installing it in the system.
The software is available in three versions that are Spoon Browser Sandbox, Spoon Selenium Sandbox, and Spoon SQL Sandbox. Spoon Browser Sandbox provides the solution for testing all versions of the leading web browsers in an online environment. Spoon Selenium Sandbox is the online system of Spoon for accessing the features of unlimited automated testing.
At last, there is the Spoon SQL Sandbox that allows the users to run SQL Server and SSMS in isolated online sandboxes. Spoon sandboxes run as a single container and enable the users to run the applications side by side without dependencies, modifications, or any other type of conflict to the host desktops.
The spoon is an excellent combination of the web-based delivery systems and the robustness of local execution at the same time. There is no need to install any software as the Spoon performs the visualization system through its web-based interface.
#37 Comodo Time Machine
Comodo Time Machine is a rollback system program based on the features of virtualization sandboxing. It is operated by the Comodo that is popularly known as providing the Chromium-based web browsers.
Comodo Time Machine has its way of making the system of its users keep and secure. Instead of creating the virtualization environment, it is based on the solution of creating a restore point. First and then allowing the users to install a new program that they want to test.
In a case of not using it, the users can easily roll back their system to the earlier potions by merely using the Comodo Time Machine. Comodo Time Machine is based on the order of imaging that is although the old technology for virtualization and sandboxing but is still being used.
Comodo Time Machine allows the users to take a snapshot of the system that is similar to creating a restore point. Then the users can roll back to the previous situation if necessary anytime. The need for Comodo Time Machine arises during the installation of large files that didn’t go just right or system testing or performing configuration based tasks.
#38 Comodo Internet Security
Comodo Internet Security is a sandboxing solution for online activities only. Means Comodo Internet Security can be used for online activities only and securing the system from online threats only. If you are looking for a sandboxing virtualization system for testing new programs, then Comodo Internet Security is the perfect option for you.
Comodo Internet Security aims to keep the system of users by adding the multi-layered security system and making it possible for the users to get the unknown files automatically sandboxed. Comodo Internet Security is entirely different from other types of internet security providers whose primary purpose is to keep the system safe and secure.
The way of working of Comodo Internet Security for providing the security and keeping the system safe from automatically installing the unknown changes is the primary function of Comodo Internet Security to perform. Comodo Internet Security delivers 360-degree security to the users by protecting by combining powerful antivirus protection tools, advanced host intrusion, and automatic sandboxing of unknown files.
#39 Hybrid-Analysis.com
Hybrid-Analysis.com is an online malware detection tool that enables researchers to find out the behaviour of malicious software in a safe environment and without the need to deploy the analyzed sample at a specific target. The goal of this tool is to provide a platform where security experts can collaborate on research and get visibility into the behaviour of malicious software without having to infect their analysis system or to run possibly infected files on their local workstations.
The website can be used by security consultant companies to fix their clients’ issues related to malware, especially zero-day threats. Users can upload files of any size to the website and find out if they are infected with malware or not. The website also provides a detailed analysis of what sort of malware has infected the file, along with a step by step explanation of how it was found.
This website works by collecting samples from all over the world, scanning them for vulnerabilities, and then providing the results for analysis by security experts in order to protect end-users against threats, whether they are based on Ransomware, Trojans, zero-day malware or any other form of cyber attack.
#40 Scanops Antivirus
Scanops Antivirus is a fully-configurable, cross-platform, security scanning and virus analyzer API that can be used by developers to embed it into their websites or applications. Unlike traditional solutions, it scans JavaScript, HTML, and CSS for viruses. That means that any site you build can be protected from viruses, even if you use a static site generator. The tool is powered by multiple tops of line antivirus engines and provides private or self-cloud hosting.
It is great for applications like web or desktop apps where you want to offer the users real-time antivirus scanning. For example, you can integrate Scanops into your application then the users will be able to scan each file that they download or receive from a user in order to make sure that they are safe.