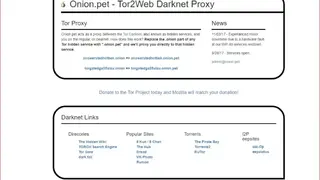
Onion.pet
Onion.pet is an all-in-one proxy that provides secure access to hidden services using the Tor network. Just all you need to replace the .onion with .onion.pet in any Tor hidden service domain and access to a website with ease.
Onion.pet permits you to get anonymous access or browse the favorite site without the need to download any software or application. This utility will accelerate the request processing automatically courtesy of having the quick and responsive caching process, and there be no request current in logs for sure.
Onion.pet Alternatives
#1 Onion.ws
Onion.ws is a completely secured darknet gateway or proxy that is providing simple access to the darknet site, and there will be no need to download or configure any new software in this regard as in the case with Tor and I2P. This web proxy is straightforward in opening Tor hidden services with either regular or non-Tor enabled browser, including Firefox, Safari, Chrome, or else.
Just all you need to replace the .onion with .onion.ws in the browser’s URL bar, and by pressing the go button, you are redirected to a darknet site. This utility is the simple yet most effective source of accessing the darknet via having the accelerated cache-backed Tor gateway. Onion.ws is doing is using robust SSL encryption and is not logging any user requests to protect identities in the best way.
#2 Onion.ly
Onion.ly is a Tor2Web proxy and gateway that permits you to have easy access to .i2p and .onion domains regardless of the need for Tor or I2P software. The platform is providing users with no logging possibilities and facilitates HTTPS-based encryption caching for faster load times. This utility is safe as far as visiting the website is concerned, and you will have complete privacy and security.
Access any hidden .onion service that also includes the new v3 addresses via simply adding a .ly at the end of the domains. It’s like a Tor2web server that is all set up to accelerate requests in a robotic manner, and credit goes to the network of the caching process provided by Onion.ly. You will see that there will be no requests that remain in logs.
#3 Tor2web
Tor2web is a top-notch utility that is designed for accessing TOR hidden services direct from the standard browser without making a connection to the TOR network. This software project providing the best means to anonymous browser the internet, and there is nothing required to use Tor Browser, just simply access to Tor Union services with complete privacy and security.
It is very easy to get started, just replace the simple .onion with things like .onion.cab, .onion.to, or .onion.direct in the URL or any domain that is freely available. Tor2web will be best if you are using it as a publisher, as it provides more reliability as far as authentication and confidentiality are concerned. Besides providing hidden access, Tor2web also provides additional services like integration and statistics for behavior analysis.
#4 Onion.sh
Onion.sh is a kind of reverse proxy that is all set to forwards HTTP requests in order to access the TOR hidden service without opting for downloading any software. Just all is needed to replace .onion to .onion.sh in the URL of the browse and get a more secured and anonymous experience to browse websites that you love.
Onion.sh is creating a private internet connection and is surfacing the strong encryption and is routing traffic of the chosen sites vai having a flexible TOR network. It is working like a Tor2web server that accelerates the request robotically courtesy of the network caching process, and there is no request logging at all.
#5 Orbot
Orbot is free to use proxy application that provides capabilities to other applications to make sure the secure use of the internet. This application is using Tor specialties to encrypt all the internet traffic and hide them through computers from all over the world. Orbot is using Tor that in turn supports you to defend against threats like privacy and freedom, confidential business activities, and state security.
Orbot is the must-have choice that seemed to be perfect in creating a private internet connection and is making the encryption stronger because the traffic bounces off several times. This means you do have a traditional way to connect directly, as with VPNs and proxies. The application prevents if someone is consistently watching connection to check for the application that is running and the websites that you have visited. In short, Orbot is a great application that routes traffic of all chosen applications with the flexible Tor network.
#6 I2P
I2P is an encryption base private network that allows you securely browser services with easy-to-use APIs from the favorite sites without mention activity, location, and name. This protected network layer is designed for teams and people that are worried about their data being collected or tracked. So, I2P is providing an anonymous connection having strong encryption on the user’s traffic. Get more improved end-to-end encryption courtesy of having the transport protocols that act as a barrier for DPI censorship.
I2P hides the server from the user and vice versa, and the traffic becomes internal to the I2P network, and traffic cannot be interacted with the internet by direct means. All the information is hidden, and there is no way to see where the traffic is coming and where it is going and is providing the complete resistance to pattern recognition and blocking.