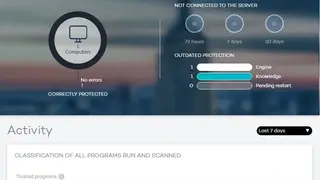
Panda Adaptive Defense
Panda Adaptive Defense is the only AI-based security platform that monitors, detects, and protects against advanced threats, including zero-day attacks. It is the next generation of threat defense solution that learns and adapts to mitigate any attack. It supports both on-premise and cloud/SaaS systems, including antivirus and security information event management tools, so a company can get the most from its investment in existing systems.
Panda Adaptive Defense is a new approach to security that redefines protection for your standard, hybrid, and cloud computing environments. It uses machine learning to build protection around what your organization really needs. It’s fast, cost-effective protection that stands up to the most sophisticated cyber-attacks. It seamlessly integrates with existing security tools – and supports other security tools like firewalls and encryptions, so enterprises don’t have to choose between multiple tools. The cloud-based service removes the burden of managing multiple security solutions and allows organizations to focus on their business priorities. All in all, Panda Adaptive Defense is a data-driven endpoint protection platform built to deploy the industry’s most advanced threat solutions.
Panda Adaptive Defense Alternatives
#1 Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is an enterprise endpoint security platform that provides Component protection against malware, ransomware, and spyware. The solution provides integrated single sign-on and multifactor authentication, a hardened endpoint through virtualization and isolation, automated security management, and threat protection. Microsoft Defender ATP has been designed to dramatically improve an MSP’s ability to detect, investigate, respond and remediate cyberattacks against their customers. It is also integrated with the new Azure Sphere platform, which helps keep people and products safe from the moment they connect to the internet.
It is a cloud-delivered solution that uses behavioral, network, and endpoint insights to stop threats in real-time. Whether you want to protect your organization from evolving malware, targeted attacks, and advanced persistent threats, Microsoft Defender for Endpoint can help. In addition to being easy to use and simple to deploy, it provides the visibility you need to stop threats before they cause harm. All in all, Microsoft has the most comprehensive cloud security platform that recognizes threats at first sight and helps protect against them with built-in threat intelligence. Combining malware protection, next-gen firewall, and threat intelligence, it gives you the power to take on any threat.
#2 Singularity Platform
Singularity is the next-generation security platform that provides the first line of cyber defense by protecting organizations from increasingly sophisticated and dangerous threats. With Singularity, companies can get visibility across their endpoints and applications so they can address security risks before they become a problem. The Singularity cybersecurity operations platform protects against threats at the endpoint, identity, and network layers. Developed by information security specialists, the platform unifies endpoint protection, threat intelligence, and network oversight at the industry’s lowest TCO.
The software delivers a single source of truth that allows its customers to understand, monitor, and remediate risks at scale. Through agentless monitoring, Singularity provides visibility into risks across containerized, virtual, and cloud-based environments. As a unified platform, Singularity empowers security teams to shift their focus to solving problems with the intelligence they gain from their environment. Any company, organization, or individual can add AI or machine learning capabilities to Singularity.
#3 Fidelis Endpoint
Fidelis is a cloud-based endpoint security platform that delivers unmatched protection against the most advanced cyberattacks for organizations across the globe. Through its pioneering and patented technology, Fidelis continuously monitors the entire attack surface of the endpoint, providing real-time protection across the full attack continuum and preventing threats that other security solutions miss.
Its flexible deployment options and a powerful set of integrated threat intelligence feeds help keep organizations safe in today’s evolving threat landscape. Fidelis is used by leading consumers, enterprises, governments, and managed security service providers to detect, prevent and respond to advanced malware attacks on all endpoints. It provides its customers with a unified view of their endpoint security controls and alerts them to both known and zero-day threats.
Fidelis Endpoint integrates seamlessly with domain controllers and existing infrastructure to provide centralized management, reporting, logging, antivirus, anti-spyware and anti-ransomware protection. It has been designed to maintain the highest possible level of performance across an enterprise network, ensuring that the network is protected from security threats without any negative impact on users’ experience or productivity.
#4 Harmony Endpoint
Harmony Endpoint is a cybersecurity software that helps businesses protect against cyber attacks. It safeguards IT infrastructure devices, including servers, desktops, mobile devices, and more. The security solution provides a security platform that features an array of security solutions, including endpoint protection, threat intelligence, vulnerability management, and continuous protection. The solution enables an organization to stay on top of threats through real-time detection and rapid response. This software also offers a single console for visibility into devices and security threats, and it continuously monitors potential threats.
With one unified platform, it eliminates the need for multiple security solutions such as perimeter firewalls, centralized AV, NAC, SIEM, DLP, and endpoint protection. The platform is easy to deploy, manage, and use. It utilizes a unique combination of patented machine learning and behavior analysis technology to eliminate advanced threats without interfering with users or consuming limited IT resources. Without any doubt, it is transforming the cybersecurity industry by providing advanced threat detection and prevention without the complexity or high cost of traditional security solutions.
#5 Panda Adaptive Defense 360
Panda Adaptive Defense 360 is a highly-accurate, cloud-native security platform that identifies the unique behaviors and characteristics of your endpoints and networks. This powerful technology can be deployed in a matter of minutes, which means faster protection and more time to focus on other IT priorities. This next-generation, purpose-built endpoint protection platform helps thwart advanced cyber threats. It combines rules-based prevention, dynamic application control, and cloud-powered threat intelligence to control malware in real-time and prevent sensitive data from leaking
Panda AD 360 gives companies the ability to adapt and protect against advanced malware, targeted attacks, ransomware, and business email compromise and removes the burden of managing multiple endpoint systems and security tools. It offers real-time visibility into known, unknown, and zero-day threats with vulnerability management and user and entity behavior analytics so your team can focus on what really matters to your business. The robust technology protects against today’s sophisticated attacks by combining the power of big data with the strength of artificial intelligence. With it, the enterprise can now have a single pane of glass to visualize and respond to security incidents across all endpoints.
#6 Cybereason XDR Platform
Cybereason’s XDR Platform combines the power of machine learning with the one-click simplicity of an all-in-one platform. The platform can handle the most advanced cyber-attacks, protect your endpoints, and take the guesswork out of security. Cybereason XDR Platform is a next-generation endpoint security platform that uses artificial intelligence to detect, analyze, and respond to cyber-attacks. XDR employs detection layers to identify and eradicate malware, including an emulation layer that can stop zero-day attacks as they are executed on your endpoints.
Cybereason is able to eliminate manual tasks to empower its analysts to focus on devising strategies against real cyber threats. It isolates suspicious files in a virtualized confinement environment to prevent file corruption and data loss. And with a host of enterprise-ready features, such as centralized management and integration with endpoint security solutions and popular SIEMs, XDR seamlessly scales up with your business.
#7 Cisco Secure Endpoint
Cisco Secure Mobility Client is a security platform that delivers the capability to create, manage and enforce security policies for all endpoints from mobile, desktop, and IoT devices. Cisco Secure Mobility, a Client security platform, relies on Cisco’s strengths in endpoint management, identity and access management, and other enterprise mobility management capabilities. The software comes with rich EDR capabilities, providing endpoint detection, threat hunting, and integrated risk-based vulnerability management from Kenna Security. The Cisco Secure Endpoint solution is a simple to deploy and manage yet comprehensive endpoint-protection platform that brings together best-in-breed endpoint protection with advanced compliance enforcement capabilities.
It provides effective endpoint protection with an out-of-the-box deployment and rich, flexible policy configuration as well as advanced reporting. Using Cisco Software as a Service (SaaS) subscription models, the solution integrates with existing infrastructure and supports some of the most commonly used productivity software. The most alluring thing about this software is its advanced investigation capabilities, providing queries to your questions. It is an end-to-end solution that provides visibility, policy enforcement, threat prevention, and response for Windows, Mac, Linux, and Android devices.
#8 Heimdal Endpoint Prevention
Heimdal Endpoint Prevention is a cloud-based security platform that provides real-time protection for end-users and systems. The solution offers a comprehensive set of technical controls, including Deep Anti-malware, Device Control, Web Threat Protection, EDR, and Mobile Security. The platform combines machine learning, behavioral analysis, and whitelisting to protect systems against the growing volume of attacks and threats. The Heimdal platform is based on a flexible model that is easily integrated or deployed on-premise, in the cloud, or as a hybrid solution. It uses a cloud-based architecture that is easy to set up, maintain, and scale.
It integrates with 3rd party anti-malware solutions such as Microsoft Defender for layered protection. The Heimdal Security Endpoint Prevention Platform uses a behavior analysis engine that learns normal activity on the system and safely auto-whitelists applications. The platform can stop zero-day attacks using the integrated machine learning engine to detect hidden threats. There are multiple features on offer that include remote desktop control, DNS filtering, vulnerability management, Next-generation Antivirus detection, email fraud prevention, email security, application control, privilege access management, and more to add.
#9 Elastic Endpoint Security
Elastic Endpoint Security is a complete endpoint security platform that provides organizations with the visibility and control they need to protect against today’s sophisticated cyberattacks. It allows organizations to detect and stop cyberattacks before they have a chance to spread internally or externally across their network. Whether the cyber-attack comes in the form of a phishing email, a malicious attachment delivered via email, macro-based malware, or unauthorized network access,
Elastic Endpoint Security provides organizations with the visibility and control they need to respond to and mitigate these attacks. Elastic Endpoint Security is a new approach to endpoint protection that offers the first agentless, software-only solution that protects an organization from any endpoints anywhere in the world. Built on the IBM Cloud, it automatically scales across millions of endpoints in real-time, protecting a company’s most important assets, including data, applications, and users. There are multiple features on offer that include machine learning support, optimized workflow, detection alert external notifications and actions, malware prevention, host data collection, centralized ingest and agent management, log categories, APM correlations, customized relevance search, and web-based support, and more to add.
#10 GravityZone Ultra
GravityZone Ultra is the best cyber security platform to secure your business data and more. It protects you against all kinds of cyber threats and protects your business’ database, network, and daily transactions against cyber-attacks. GravityZone Ultra helps you keep your business safe from financial data loss, cyber-attacks, and much more. This endpoint security platform can detect and stop in-memory attacks. It detects both everyday and advanced threats from file-less malware and insider attacks across all endpoints, servers, and mobile devices. With built-in artificial intelligence, Fidelis Endpoint Platform helps protect against even the most evasive malware in real-time – whether it’s known or unknown.
GravityZone Ultra is a security platform for the cloud. Based on an embedded security engine, it can monitor, block and detect threats across your application portfolio, providing visibility into threats and an end-to-end view of Risk and Compliance. The software comes with extensive advantages like cross-endpoint correlation, advanced prevention capabilities, low overhead incident investigation and response, endpoint risk analytics, network attack defense, cross-platform coverage, layered defense, and much more.
#11 CyCraft AIR
CyCraft is a security platform that lets you streamline your organization’s cybersecurity, compliance, and security programs. The automated software covers a wide range of cybersecurity concerns: from logging, alerting, and access rights to penetration testing, phishing, and managing audits. We offer a full suite of tools to help you protect your business from external threats and internal risks. The software notifies and alerts your team members about suspicious activity, giving them the opportunity to prevent real worldwide cyberattacks in the making.
It automates the management of your security programs so you can focus on what really matters – your customers. The software is on a mission to provide security in the hands of every user, enabling them to make informed decisions about their online safety. Compromise assessment, incident response, managed detection and response, secure from home, auto-triage alerts, automated investigations, eradication threats, sophisticated adversaries, and more are the things that make CyCraft AIR a reliable security platform.
#12 FireEye Endpoint Security (HX)
FireEye Endpoint Security (HX) is a software-as-a-service (SaaS) solution that provides real-time threat detection and protection for your endpoints. The software is designed to detect advanced malware, zero-day attacks, and other types of attacks that have previously evaded detection. With HX, organizations can provide the protection needed to safeguard sensitive information from compromised endpoints.
FireEye Endpoint Security (HX) is the only solution that stops advanced threats at the endpoint that have infected the network. HX, FireEye’s next-generation endpoint protection solution, provides organizations with a powerful set of defense-in-depth features to stop dynamic, sophisticated, and targeted malware attacks before they enter your network and block malware and file transfers if a breach has already occurred. The software provides best-in-class protection to your organization courtesy of having intelligence-led protection, detection, and response. The rich features are blocking common malware, stopping advanced threats, halting application exploits, detecting endpoint threat activity, stream alerts, endpoint detection, behavioral analysis, centralized management system, and more to add.
#13 BlackBerry Optics
The BlackBerry Optics is an independent analysis of software designed for firmware or hardware. It also offers free tools, methods, and other resources to help product developers and independent security researchers conduct their own research into new vulnerabilities. It comes with a comprehensive EDR approach that makes sure you have no response latency. It is a decisive point in spotting the difference between the major and minor security events.
With the best-in-class AI, you will be able to identify security threats and trigger automated responses on a device with security and context-driven threat detection rules. It uses a standardized methodology to coordinate disclosures and remediation efforts across the ecosystem and to rapidly investigate and resolve reported vulnerabilities while also providing clear and credible advisories. It is the only unified platform that protects every stage of a company’s digital life.
It enables security teams to deploy and manage complex enterprise mobility and mobile productivity solutions across personal and corporate data. The rich features are custom detection, crypto-mining detection, advanced scripting visibility, custom detection rules, advanced scripting visibility, deep insight with maximum retention, and more to add.
#14 Absolute Platform
Absolute is a next-generation endpoint security platform that gives you the power to identify advanced attacks and stop them before they breach your network. The Absolute Endpoint Security platform integrates agents with multiple antivirus engines in a single console for cross-engine threat analysis. It enables real-time protection of workstations and servers in the cloud, including Linux environments, from malware and zero-day threats. It creates a security bubble around every endpoint, protecting users from both known and unknown attacks. And because it’s cloud-based, it’s able to adapt and learn as attackers continually change their tactics.
The company offers a cloud-based or on-premises platform for endpoint security, data leak prevention, and privileged activity monitoring, as well as mobile application management for iOS and Android devices. The rich features are a customized dashboard, measuring device usage, automating hardware inventory, firmware protection, and remote scan, assessing security posture, running power shell, 3rd party integrations, remote freeze devices, enabling firmware protection, and absolute control mobile application, and more to add.
#15 WithSecure Elements Endpoint Detection
WithSecure, EDR is a comprehensive security solution that features a powerful endpoint protection engine, advanced threat detection, pre-breach investigation, and incident response capabilities. It provides real-time visibility into the status of devices on your network and allows your security team to work faster, more securely, and with more context. WithSecure products are designed to detect and analyze malicious behavior happening on endpoints. WithSecure solutions also help organizations investigate and remediate network-level breaches and automate their incident response procedures using their own SOC staff.
It provides a built-in, turnkey solution that analyzes every transaction from endpoints with a single, shared security policy and automatically applies the most appropriate response to eliminate threats. It uses a variety of AI techniques, including machine learning and decision trees, to protect against today’s advanced threats. With this capability, customers can enclose vulnerable endpoints in a secure environment and protect them from being infected by malware or accessing fraudulent sites or applications.
#16 Tanium Core Platform
Tanium is the core platform that powers McAfee Endpoint Security and Control, bringing to market a new approach to endpoint security. With it, organizations gain real-time visibility into their environment and the ability to respond to threats rapidly. Because Tanium is cloud-based, it is easy to deploy and manages tens of millions of endpoints across the globe for organizations of any size and scale. It also provides a highly secure collaboration platform to share threat information among different organizations, as well as a full reporting suite that lets teams track investigation results and productivity.
Tanium uses Big Data analytics, machine learning, and artificial intelligence to provide real-time visibility into your entire network at the endpoint, delivering an unprecedented level of protection and actionable intelligence. It consists of a policy engine, centralized management, and Threat Analytics capabilities to enable immediate threat mitigation, forensic investigation, and remediation.
#17 Tachyon
Tachyon is an enterprise-grade endpoint security platform. It continuously monitors the host, the network, and all user behaviors in real-time. It immediately detects and identifies abnormal activities that signify an attack and provides the context of the threat to business analysts. By providing a holistic view of an organization’s endpoints, Tachyon enables analysts to detect and respond to threats in a faster and more effective manner than traditional endpoint antivirus to improve business continuity and reduce business downtime.
The security platform is designed to identify and prioritize risks while preventing the massive false positives that plague legacy technologies. It leverages the power of AI and machine learning to automate the security analyst’s search for hidden threats, so organizations can spend less time cleaning up after attacks and more time responding to them when they actually occur. Tachyon’s powerful analytics help security teams quickly isolate suspicious events, conduct deeper investigations, and take action. This makes it easier for organizations to provide a level of security that exceeds compliance requirements without impeding employee productivity.
#18 Symantec Advanced Threat Protection
Symantec Advanced Threat Protection is a new generation of threat protection that proactively protects your endpoints from cyberattacks. This sophisticated new approach doesn’t rely on steady-state inspection of files and data, nor does it collect and track user data in the cloud. Instead, ATP is designed around the premise that every organization faces a different threat landscape and thus must have a different security strategy. It facilitates you with robust email threat detection and response, web isolation, encrypted traffic management, content analysis and sandboxing, network forensic security analytics, intelligence service, and more to add.
Symantec Advanced Threat Protection protects your organization against the most advanced cyberattacks, including zero-day attacks and the entire spectrum of malware. Symantec’s deep expertise in email security and advanced threat protection gives you superior threat intelligence, allowing you to focus on your business. It allows enterprise security teams to prevent data loss while remaining active defenders that can stay ahead of new attacks and react faster to evolving threats.
#19 CrowdStrike Falcon Complete
CrowdStrike Falcon Complete is a managed detection response that helps you stop breaches from entering your system. It monitors the system every second via threat hunting, monitoring, and remediation techniques which are backed by its proprietary breach prevention warranty. It provides the actionable intelligence and skilled expertise required to provide comprehensive endpoint security from beginning to end. With this platform, you can assign, manage and stop the incident response of your endpoint security to its proven team of security experts.
In order to protect your organization in the age of digital transformation, downtime and business disruption must be minimized while you’re working to resolve any detected threats or breaches. CrowdStrike Falcon Complete provides the fastest incident response solution in the industry with a 24/7 SOC consisting of an Enterprise Incident Response Team and managed response services. You get a 360° View to control every aspect of your endpoint security and full support from the moment you acquire it.
#20 Secureworks Red Cloak MDR
Secureworks Red Cloak MDR is a solution that offers endpoint detection and response services with 24/7 threat hunting and incident response in a single solution. It provides a starting point for analysts and security operations professionals to detect, investigate and respond to advanced cyber-attacks. In short, you get a centralized console that provides an overall view of your entire environment. It’s designed to be integrated seamlessly with leading systems management platforms, such as IBM Tivoli and HP Automic, for greater efficiency and more comprehensive security.
In addition, it provides actionable intelligence on data exfiltration and ransomware attacks. Moreover, there is actionable guidance to remediate, which helps you eradicate the threat earlier in the kill chain to prevent or minimize data loss. Collaborate and stay on the right track with periodic reviews of your security posture. Discuss observed activity and findings, security trends, and best practices to further accelerate your security program.
#21 Blackpoint Cyber MDR
Blackpoint Cyber MDR offers state-of-the-art cybersecurity solutions, including Managed Detection and Response service. It does not only detect threats earlier than breaches but also provides an actual response rather than just an alert to keep your and your clients’ networks safe from widespread damage. True 24/7 MDR will help secure endpoints, servers, cloud infrastructure, and more. This level of protection is unprecedented among cybersecurity providers on the market today.
Blackpoint automatically detects 98% of all attempted breaches before they even happen. This unique detection capability allows you to respond to attacks quickly and efficiently, averting catastrophe for your clients and freeing up your time to focus on growing business. Its patented technology is built from the ground up to give you the ability to continuously monitor and respond to the modern threat landscape. All in all, Blackpoint Cyber MDR is a great tool that you can consider among its alternatives.
#22 Arctic Wolf AWN CyberSOC
Arctic Wolf AWN CyberSOC is a security management solution created for all sizes of businesses. The platform provides all the leading security tools, services, and features to make your network secure from all kinds of threats. It comes with 17 security operations technologies that can enhance overall security strategies.
It starts at a very basic level, and now it is used by thousands of users around the world who can use it to make their network secure. The solution collects and enriches endpoint, network, and even cloud telemetry and then intelligently analyzes it with several detection engines to deliver 100% security. There is also a machine learning and custom detection system that help you deliver personalized protection.
Like other similar solutions, it also offers several security products that you can apply to all your devices, networks and, even clouds. Arctic Wolf AWN CyberSOC is a commercial security solution that offers multiple price plans.
#23 SentinelOne
SentinelOne is the leading solution providing company that offers the security of networking over endpoint protection. It is the topmost used protection service provider that works in a sophisticated way. The solution is designed for enterprises in education, finance, healthcare, and energy industries.
It is an IT network security solution that implements a specific type of computer network security. The topmost used integrated features of the program include real-time endpoint protection, activate detection and quick response, cloud-based IoT discovery and control, and native cloud-security.
The data stored on the cloud is accessible by private servers by using hybrid cloud technology. Multiple algorithms integrate for encryption module, the devices defend themselves and heal by any attack, and it provides file integrity monitoring, protection, and compliance.
The core function of SentinelOne includes auto-immunize, security Integrations, lightweight and holistic agents, dynamic whitelisting and blacklisting, and much more. It provides technical support, which is available every time to solve any queries.
#24 Trend Micro Managed XDR
Trend Micro Managed XDR solution provides automated risk recognition that comes with MDR for endpoints, email, cloud workloads, servers, and networks. It’s the next step in the evolution of on-premises managed cyber defense. It provides expertly managed threat detection capabilities in addition to internal security efforts, allowing companies to take ownership of their cyber resiliency. The main features of the product include Automatic multi-engine signature updates, and adding custom rules by the managed security service provider automatically extends coverage over existing protection.
You can also deploy additional threat intelligence through your own global threat intelligence network. New signature engines are regularly added to ensure the firmware is always up-to-date against the latest threats. One of the strengths of Trend Micro Managed XDR is its ability to be deployed quickly with a lower total cost of ownership than is possible with traditional approaches. The solution includes the scalability and flexibility to handle the needs of the largest enterprises and supports regulatory compliance.
#25 Sophos
Sophos is a computer and cloud security provider company. The company provides different layers of encryption and a solution to access and transfer data to multiple servers. The data is accessible from connected multiple public servers.
Sophos is the most prestigious cybersecurity proving company, and there are various modules in its services such as endpoint protection, evolved firewall, PC protection, public cloud visibility and threat response, and more.
The software works on multiple operating systems and has tons of functionalities and features, some of the features include consolidated network security platform, advanced threat protection, customizable web filtering, simple management, flexible deployment, and a few more.
The interface of the programs is easy to configure, and it offers multiple users interactions modules. The security aspect of Sophos check the data on the endpoint, detect traffic, provide a behavioral analytic report, and integrated endpoint and network.
Managing and accessing the data is easier than before, and automatic removal of third-party endpoint security products is automatically done in real-time. It is not free and provides a subscription module.
#26 Ngrok
Ngrok is one of the most used software for cloud computing, and it provides solutions for web integrations. It is a tunneling software that works on multiple platforms that establish secure tunnels from a public endpoint such as the internet to a locally running network service while capturing all traffic for detailed inspection and replay.
The software is efficient in work and provides tons of features, it also provides end-to-end protection, and the data is accessible in multiple forms. It passes through the firewall to give you secure access to the server. The threat detection is the most used module because the data analyze the data packets on the endpoint and gives a report. The integrated smart AI structure keeps the data if it is secure.
The core features of the program offer multiple functions like secure tunneling, fast configuration, and access, password protection, Websocket support, automate Ngrok via API, Shared account access for teams, and much more. The interface is easy to use, and the configurations are easy. The solution comes with a subscription plan. It is best for both small businesses and large enterprises.
#27 Kaspersky Endpoint Protection
Kaspersky Endpoint Protection does exactly what it stands for, that is, providing endpoint security for business. The software solution is provided by Kaspersky, and the company is providing many other functionalities regarding networking. The software works on multiple operating systems and has tons of interesting features.
The core aspect of the program delivers adaptive protection against known and unknown threats, reduces your exposure to attacks, helps prevent loss or theft, secures loose ends, provides a streamlines security management, and much more.
The cost-effectiveness of the program is approachable, and it is good for enterprise users as it provides endpoint security. The interface of the program is easy to use and offers good user interaction. The configuration module of the program is smart, and it saves all the settings for later use.
Kaspersky Endpoint Protection also provides custom-tailor security for any organization that requires small integrating or deals with protected data solutions. It ensures efficiency, gives the best possible protection, fits into existing infrastructures, and more.
#28 Trend Micro
Trend Micro is an IT security company that provides software solutions and hardware for your networking. The software for the protection of data on the server and end-to-end users. It provides a solution for both home-based and organization-based platforms. It works with three main modules that are hybrid cloud security, network defense, and user protection.
Trend Micro can optimize the security of the cloud services and integrate with them. The main functions of Trend Micro are the plug-in manager and plug-in solutions. They have different workings, the manager controls the installation, deployment, and management aspect, and the plug-in solution provides programs and native OfficeScan features.
The other features work in different areas and collectively give a remarkable solution for security and user interactions with the data and the server. A few features of Trend Micro include centralized management, security risk protection, damage cleanup services, device control, security and policy enforcement, and much more.
#29 Carbon Black CB Defense
Carbon Black CB Defense is software offered by a company named Carbon Black. They are known for providing layers of encryption modules on the endpoints to protect the data. All the functions are cloud-based and linked to the servers. Carbon Black is the child product of VMware, and it is the best security and networking hardware provider.
The interface of the software is user-friendly, and it offers next-generation antivirus with endpoint detection and response, and it passes through a cloud-native endpoint protection platform. The main functions it offers are protection form predicted cyberattacks, stop malware, block the data from transfer when the line is not secure.
Carbon Black CB Defense saves the unfiltered data from every endpoint which analyze the data for potential threat, works while offline, run analysis against signature reputation, automatically store the data after analysis, show the overtime progress and saves the data. Carbon Black CB Defense gives quick response, takes less memory in CPU, and operates at a scale.
#30 FortiClient
FortiClient is a client-based software solution that offers security features for the desktop. It is also used in servers and connections and provides IPsec and SSL encryption, WAN optimization, endpoint compliance, two-factor authentication, and other security protocols. The interface of the software is easy to understand, and it provides tons of functionalities and features.
The cloud-based protocols are connected and give global cloud intelligence that links with behavior dynamics threat detection securing the data and preparing for disaster recovery. It further links to advanced threat protection and saves the data from harm.
The primary features it provides are the unified end-point security, end-to-end threat visibility, advanced protection layers of encryption, simplified user interface, and integrated recovery palm that acts as an AI standalone operating system for securing the data.
The security integration is easy to understand, and the user has no problem configuring the system. With the automation feature, it saves and improves the user’s settings. FortiClient comes with a separate vulnerability dashboard, Windows AD integration, dynamic access control for compliance enforcement, automated response, telemetry, and more.
#31 Symantec Endpoint Protection
Symantec Endpoint Protection is the endpoint software for protecting the data and preparing for a DR plan. The main function of the program is to provide layers of security to protect the data. The software is the product of Symantec Inc.
Symantec is known to be the security provider for network connection. It is best for organizational use and provides a backup plan for both malware and targeted attacks. The interface of the program is easy to use, and it offers many interesting features.
The main function of the program includes client-end installation, management server features, documentation tools, and more. The protection feature of Symantec Endpoint Protection offers intelligent threat cloud service for client installation, SONAR/Auto-Protect, an emulator for packed malware, scheduled and on-demand scans support, client submissions and server data collection, and more.
Symantec Endpoint Protection runs on multiple operating systems and offers different functions for endpoint protection on OS. The database it uses is SQL Server 2014 SP2. The program is not free, and it does not offer any trial version.
#32 BigFix
BigFix is one of the most sophisticated and leading hyper-cloud infrastructure website which gave them backdoor access to IBM Inc. It is the best option when it comes to controlling the networks and servers. The core functionality of the software that provides the solution for securing the data on servers.
It is the best solution for the organization. The main thing BigFix focuses on is the lifecycle that provides agent-based tools that provide virtual tools for visibility into the state of endpoints and find the solution to the problem. The main features include OS development, power management, remote control access, server automation, software distribution, and many others.
It saves the data and gives access via end-to-end virtual point using the public servers, creates reports of the inventory, and more. The primary function of BigFix is mitigating the harmful malware on the endpoints, and it does not depend on the OS it is running. It improves the response time, efficiency, cost, and complexity, and gives functionality and configurable setting to secure the endpoints.
#33 Palo Alto Networks Traps
Palo Alto Network Traps is a cloud-based management service that provides end-point security, which stops threats and prevents end-points infection through blocking malware, ransomware, and exploits. The software works with the legacy of antivirus replacement that secures end-point with the multi-prevention approach and saves laptops, desktop, and servers from viruses. The software is facilitating enterprises with next-generation firewall, centralized network security management solution, and security subscriptions.
The software is providing essential security features such as computed security, identity security, network protection, visibility, compliance, and governance. Palo Alto network traps come with in-depth documentation that permits adequate information on how personal information captured, processed, and stored within traps and its associated services. The software dispenses multiple services that are end-point protection, detection and response, threat intel management, network traffic analysis, and more to add. There are various resources available that permit the authentic use of the software and its control.
#34 CyberArk Endpoint Privilege Manager
CyberArk Endpoint Privilege Manager is an endpoint security platform that allows you to protect all endpoints and apply the integration without disrupting the network. The solution enables organizations to protect critical data and applications against cyberattacks, advanced persistent threats, and insider threats by enabling the least privilege to applications and data.
This unified solution proactively secures privileged accounts and the sensitive data they access at the endpoint, eliminating the need for security teams to adapt to changes in privileged access management. CyberArk Endpoint Privilege Manager provides zero-touch policies that can be deployed immediately, with no user intervention required. For mission-critical applications, it allows policies to be deployed at an application level, maximizing security and ensuring that business processes aren’t interrupted.
To ensure that privileged accounts are never mismanaged, the manager supports hundreds of native business applications and third-party solutions. Using automation to enable rapid deployment and continuous monitoring, EPM is a secure and efficient solution for managing privileged accounts, from initial provisioning to ongoing compliance.
#35 Symantec End-User Endpoint Security
Symantec End-User Endpoint Security is an endpoint protection solution that lets you defend, secure, and remediate traditional and mobile endpoint devices. The platform is embedded with ML and AI to optimize security decisions. It provides comprehensive endpoint protection and eliminates the need for multiple security products. Deploy Symantec End-User Endpoint Security on any endpoint device, PC, Mac, Android, or iOS mobile, and protect against viruses, threats, and data breaches.
Symantec End-User Endpoint Security solution is for small and medium businesses with 100 or more employees. It protects your endpoint devices against modern cyber threats through intelligent behavior-based detection, machine learning models, and cloud automation, making security simple and easy for you to use. Whether your critical workloads operate completely in the cloud, in on-premises data centers, or a hybrid combination, it can easily discover, protect, and monitor all workloads.
#36 McAfee Endpoint Security
McAfee Endpoint Security is an endpoint security platform that lets you manage and respond to cyber-attacks and threats with proactive defenses and remediation tools. With this, organizations can detect and contain threats quickly, contain data loss using encryption technology, prevent costly downtime by quarantining endpoints, monitor and manage endpoints remotely with comprehensive health reporting, and accelerate incident response with rapid remediation from a single console. McAfee Endpoint Security prevents malware infections on devices, protects data wherever it lives, and automates responses with increased visibility and control.
The solution combines the protection of next-generation antivirus and endpoint detection and response with innovative automation, orchestration, remediation, and reporting capabilities that enable customers to respond to and manage the threat defense lifecycle with proactive defenses and remediation tools. Minimize alert fatigue and make sense of data through powerful AI-guided Investigations and reduce mean time response through high fidelity detections to prevent attacks from achieving their objective.
#37 Sangfor HCI
Sangfor HCI is a hyper-convergence solution infrastructure that is the best solution providing a platform that gives hardware facility for data access and server storage. It is the biggest on-demand solution for continuous present growth and consists of many interesting models that can upgrade the business protocols and save the data on the servers.
It is easily accessible by a hyper cloud system that moves from public cloud services to the protective cloud server and gives the encryption there in any public server in which you are connected and give you the dedicated line connection for secure access.
Sangfor HCI comes in various services, and it also provides the hardware access for its users to directly access the internet, so the business is not affected and always secure. Given the interface of the operating system, it is easy to use and provided guided steps provided by Sangfor HCI itself for easy navigation. It provides a step for integration and one-click deployment with modification.
#38 Ivanti Endpoint Security for Endpoint Manager
Ivanti Endpoint Security for Endpoint Manager is a top-of-the-line security management platform for your infrastructure. It helps you estimate, actively monitor, remediate, confirm, protect, and strengthen your network infrastructure and resources. The solution provides virtual security management and hardware independence through an agentless approach. Ivanti Endpoint Security for Endpoint Manager offers a single management console to proactively manage the health of your endpoints and network while also reducing your IT costs and allowing you to work more efficiently.
It combines identity-based management and control, endpoint protection, and next-generation firewall capabilities. Proactive security protection, configuration, and compliance policies are based on the identities of devices connected to your network, enabling seamless management of endpoints, servers, and everything in between. All in all, Ivanti Endpoint Security for Endpoint Manager is a great service that you can consider among its alternatives.