ProxyCrypt
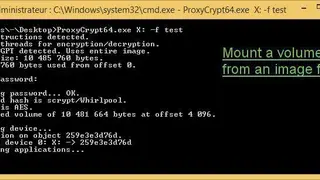
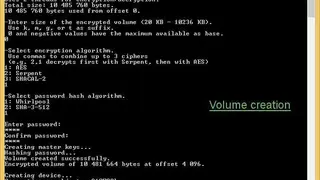
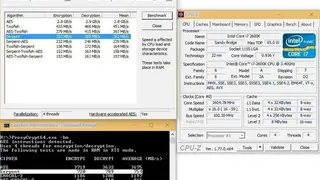
ProxyCrypt is a resistive command-line tool that allows you to create resistive volumes within the hard disk or a file. The software provides on-the-fly encryption that legitimates you to use the encrypted volumes as normal ones. ProxyCrypt is easy to recompile and is made for advanced users, and benefits you with its accuracy and lightweight. You can create encrypted volumes at any location, and it does not matter at the beginning of a partition or a file.
Now you have much more convenience and reliability with improved performances with SSE2 optimization, AES instruction, and asynchronous support for reading and write. The software provides in-depth protection against keyloggers, and you have extreme support of key files in case of conjunction or password replacement. There are more features on offer that are auto-unmount, Scrypt for more speed, XTS mode, extended path image file support, and more to add.
ProxyCrypt Alternatives
#1 SafeHouse Explorer
SafeHouse Explorer is a highly resistive encryption tool designed for internal and external drives. The software-based on Twofish 256-bit encryption technology permits you to create volumes on your drive that are invisible to others. SafeHouse Explorer provides the necessary security to your confidential information and documentation to get them out of the wrong hands. You can encrypt any file like images, videos, databases, and more to store them into virtual volumes, and whenever you require the files, you can decrypt them easily.
The interface is highly intuitive, and you have an additional drag and drop feature to store files more conveniently. The software legitimates you in sending volume to the user to open them in another computer via providing a password even the program is not installed. Furthermore, SafeHouse Explorer is also useful for the files stored on portable media such as USB sticks, and you can access them directly.
#2 Steganos Privacy Suite
Steganos Privacy Suite is an all in one data protection software that allows you to add privacy to your confidential documents and files. The software comes with the best approach to safeguard your business records and TAN lists to a separate location where no one accesses them. The software encrypts your folders and files and adds a password that makes your documents always remained safe in case you lost your device.
Steganos Privacy Suite is making its mark with a structured user interface and is known for its professional security package that permits you to use it with ease. The software protects all the sensitive data either on PC, in the cloud, or in the network courtesy of the 384-bit AES encryption and Hardware acceleration with AES-NI. Furthermore, the encryption performed by the Steganos can never be cracked that enhances its reliability to use it everywhere.
#3 Knox
Knox is intelligent defense-grade security software designed by Samsung that comes with many built-in privacy features. The software provides real-time device protection of the moment it gets turned on, and your data will never fall into the wrong hands. Knox comes with the managed container in which all the encrypted data is stored, and you can set what to do with the data and what type of data can be accessed.
The software provides an extra layer of security to protect your smartphone from malware and remote attacks. Your all the confidential files, credit card transactions, passwords, health data, and more always remain safe and secure, and you can set new dimensions to your business to do what matters the most and take care of everything that needs to be secured. Moreover, the data is securely encrypted by default, and all the personal data can be completely isolated, so you can make sure to keep the sensitive privacy out of reach from others.
#4 Advanced File Security Basic
Advanced File Security Basic is a free to use software that legitimates to save your important and confidential information with real-time encryption. The software allows you to make containers or folders where your encrypted files get stored. Your data always remain secured in case of any theft or loss of the device, and you can save your documents via using a password. Advanced File Security Basic allows you to decrypt the files whenever you need them quickly.
The software is easy to use and lightweight, and you have a simple procedure to start the preceding. You need to choose files, and with the right-click, you can either encrypt or decrypt them and, after selecting any action, insert a password. Advanced File Security Basic is providing you many elegant features that include multiple encryption options, use a USB device to unlock files, configure a USB key, solid reliability, a robust security layer, and more to add.
#5 WinGuard Pro
WinGuard Pro is a reputable software that allows you to safeguard your applications and programs on your desktop with password protection. The software provides an extra layer of security to your Windows system, and you can secure any application and software install on your operating system. You can lock any app with the password, close software installations, administrator tools, hide drivers, and lock program installers.
The software has a proper scanning system for programs with the ability to blacklist programs. If there is a display of a matching screen, then WinGuard Pro stops the application and shows a password prompt window. Furthermore, the activation is simple and easy, and you can use a free trial or purchase it for unlimited usage.
#6 Exocet
Exocet is a reputable software that allows you to perform encryption via creating folders and stored them with encrypted files. All your confidential data, notes, files, and other things are securely saved into your virtual volumes, and at any time, you can decrypt them with the command line parameter. The software comes with a robust encryption standard that makes your data impossible to access, and you have everything that is simple to control access.
The software hide folder as many on your hard drive and can be revealed with the practical key. Exocet is free to use and has an easy setup and fast response to make it up and running in a matter of no time. There are no essential requirements at all, and you can use it on any advanced windows system efficiently. After done with the procedure of Command Prompt, Exocet automatically encrypts the targeted folders.
#7 R-Crypto
R-Crypto is smart data security and disk encryption software that allows you to secure your sensitive information via strong encryption. The software creates a virtual disk using the cryptographic infrastructure, and encrypted files are stored on the virtual disk, and no one can access it. R-Crypto is easy to use and provides a robust approach for all the confidential data, a notebook, or a removable storage device to protect them against unauthorized access.
The software allows you to either encrypt and decrypt the files and your data, and if someone wants to access the data, then the user must have to provide a correct password. R-Crypto is matching the standards with AES encryption with key length up to 256-bit. Multiple features are auto connected encrypted disks, safe and reliable, intuitive interface, change the size of the encrypted disk, access to most performed actions, and more to add.
#8 AreaGuardNeo
AreaGuardNeo is an exceptional software utility that allows you to secure your data to get it out of the hands of unauthorized users. Your stolen and miss used data either by an external or internal source always remained safe. Now you have better control over the sensitive information of your business or any administrative information. The software effectively managed damaged tokens, corrupted settings with the rescue wizard, and resolve unsuccessful logins.
AreaGuardNeo is featuring complete support with its easy remote deployment, monitoring, and enforcement of the security policies. The software is the right choice for your organizations that needs their data, and information must be protected over hard drives or LAN or any external devices like removable storage devices. There are multiple features on offer that are minimum system requirements, quick response, real-time security status, virtually transparent operation, encrypt data on portable devices, and many more to add.
#9 Kruptos
Kruptos is professional encryption software that allows you to protect your password and files like images and documents with 256-bit encryption. All the sensitive information can be locked in a matter of no time, and you can protect photos, credit card data, movies, tax returns, or any other private information. Your files are always secured in case your computer is stolen or broken, and once the files are encrypted, they can be accessed from anywhere.
When talking about computability, encrypted files are fully compatible between Windows, USB drives, mac OS, and Android. Kurptos is making its mark with its Cloud encryption for Dropbox, Apple iCloud, Google drive files, and Microsoft one drive, and you also have the option of data shredding. Courtesy of the inbuilt secure note editor, you can create, organize, and keep your notes safe and secured. There are multiple features on offer: PDF encryption, sending encrypted emails, AES support, password analyzer, and many security features to add.
#10 Challenger
Challenger is a complete portable encryption software that allows you to secure your files and documentation via encryption. The software ensues with easy use and works well on all Windows systems, and can be used on portable USB drives and SD cards. Challenger software brings a reference test that efficiently detects program manipulation, and you have a real advantage of deleting the original data securely.
Challenger uses a strong Stream Cipher for encryption of data and directories, and you can set a password of various lengths. The software is designed for local data protection and to secure communication over a network, exceptionally closed systems. The software is not only going forward because of its secure encryption algorithm but also for easy use. You have the choice to either of a multi-user or portable version on an SD card or USB device, and there is no need for the runtime of library and system updates.
#11 CyberSafe Top Secret
CyberSafe Top Secret is an intelligent software program that comes with advanced encryption algorithms for protecting sensitive information. The software provides efficient tools that can be used for all the work with information such as protection of confidential information, creation and verification of digital signatures, and security of email correspondence. CyberSafe is dispensing an extra layer of protection with Cryptographic keys available in tokens, and you can keep your private key with you instead of leaving it on the PC.
The software facilitates the user with Public key infrastructure encryption that legitimates you to seamlessly encrypt computer hard disk partitions, hide logical drives, and create a virtual encrypted disk of any size. If you want to encrypt network folders, then encrypting and decrypting actions are performed on the user side, which, in turn, provides reliable protection via encryption on the server. CyberSafe does not need installation on a file server, and if having incorporated space, then you can protect information on network storage via NTFS.
#12 Steganos Safe
Steganos Safe is an elegant encrypted software that effectively protects all types of sensitive data on your operating system. The software encrypts the data either in networks or in the cloud and comes with AES encryption support. Steganos Safe allows you to secure your business records, confidential documents, and the TAN list by placing them in a safe location. The software is highly recognized because of its professional security software package that is intuitive and easy to use.
It is a kind of digital vault that adds more protection to reports, family photos, notes, and any other sensitive information. You have a highly secure encryption courtesy of the multi-core support with 384-bit encoding. There are multiple features on offer that are optimized user interface, more improve brute force protection, backup integration, two-factor authentication, easy configuration of safes, and more to add.
#13 SSuite Agnot StrongBox Security
SSuite Agnot StrongBox Security is an elegant and reliable software program that uses Ciphers to secure documents, files, or text messages. The software-based on advanced technology and can be run on all Windows systems, either 32-bit or 64-bit. The operating procedure is more straightforward than ever that starts with the image upload, and you have to select a Cipher mode, then enter your password, and that’s it.
The software legitimates you to encrypt or decrypt files with one click, and you can set unique passwords using an internal random key generator for un-shatter encryptions. You can use the password of various character strings in length, and if you want a secure transmission over the network, then you can save the text message inside a text file. Furthermore, the software is lightweight and is completely portable, which does not need to be installed.
#14 Gostcrypt
Gostcrypt is an all in one virtual disk encryption software that allows you to create containers to store them with the encrypted files. The software protects your data and also the hard disk and USB devices with the password, and your data will always remain secure in the case when you have lost your USB devices.
There is a block chipper algorithm using the 256 Bit key, and this key is divided into 32-bit subkeys internally. The S-box is modified during the keying process that, in turn, provides options of the algorithm by the user. Gostcrypt provides much more resistance to the Kwon attacks, and in the new version, you will see a Grasshopper algorithm in Gostcrypt.
#15 EDS (Encrypted Data Store)
EDS is a reputable virtual disk encryption software designed for Android that helps you to save your files in the encrypted container. There are various supported containers to store encrypted files that are VeraCrypt, EncFs, LUKS, TrueCrypt, and CyberSafe. EDS can be operated either on mounted or non-mounted mode. In the Non-mounted mode, you have a built-in file manager, and you can open a file that can be viewed directly from the container.
When it comes to the mounted mode, the container links with the file system of the device and do not need temporary files to encrypt or decrypt files inside the container. Various systems are supported in a mounted mode, such as EXFAT, EXT4, FAT, EXT2, NTFS, and more to add. Multiple features are streaming media from the container, opening containers from a windows network share, fingerprint unlocks, dropbox container synchronization, and more. The software is available in an open-source light version, but if you have to enjoy full functionality, you should go for the paid version.
#16 FreeOTFE
FreeOTFE is an all in one software designed for on the fly encryption that can efficiently run on your computer. The software creates a virtual drive within a file or partition to automatically encrypt anything written before storing it into a hard disk or USB storage device. FreeOTFE is highly portable, so it does not need to install in the operating system. A FreeOTFE Explorer system is also permitted to access the FreeOTFE volumes without going for installation, and surprisingly, there are no administrations required.
The software legitimates you to create more than one or more virtual disk on your PCs, and everything written is securely and transparently encrypted on it. FreeOTFE is easy to use, and for your convenience, a full wizard is included for creating new volumes. Multiple features are multi-language support, option support for smart cards, support for encrypted Linux volumes, improved flexibility, and more to add.
#17 LUKSUS
LUKSUS is intelligent encryption software that allows you to encrypt your files, virtual container, USB sticks, and hard drives. The software is using the internal encryption mechanism of your operating system to encrypt files that act as the frontend. There are multiple containers for the encryption that are LUKS, GELI, FreeBSD, LUKSUS, and also provides support for GNU Privacy Guard and OpenSSL for the encryption of single files.
LUKSUS is easy to implement to encrypt storage media in Linux, such as USB devices, hard drives, and SD cards. The software works on Linux, DragonFlyBSD, and FreeBSD, and it is tested on the distros like Debian, Ubuntu, ArchLinux, FreeBSD, and DragonFlyBSD.
#18 Zed!
Zed! is an all in one encryption software that allows you to encrypt your sensitive files before sending them to others. The software functioned on the advanced technology, and once you encrypt your files, only authorized recipients will be able to decrypt them via either passwords or certificates. The software elegantly encrypts your e-mail, so they remained secured before sending them to customers or others.
Zed! Handsomely protects your USB devices just by adding a zed file on it that makes your data always remain protected in case of loss or theft of USB devices. You have one or more Zed! Containers to store your encrypted files, and later you can access them via using the password. The software provides you with multi-lingual support and is implementing an AES encryption algorithm that makes sure a high level of security. Furthermore, Zed! Brings the possibility of transporting a whole tree structure, and you have no limitation over the volume.
#19 RealCrypt
RealCrypt is encryption software that is free to use and brings functions to secure your files via performing encryption. The software elegantly creates a virtual disk on which the encrypted files are stored and mounts it as a real disk. ReakCrypt is quite capable of encrypting whole hard disk partition or storage devices like USB flash drive.
The software is very reliable, having automated, transparent, and real-time on-the-fly encryption. RealCrypt is providing two levels in which you are having glib deniability and hidden volume. Furthermore, apart from the previous versions, more improvements are made in the current version, but functionalities remained the same.
#20 LUKS Manager
LUKS Manager is an agile software designed for on-the-fly encryption, creating virtual folders on android devices, and storing them with encrypted files. The virtual folders can be set either mounted and unmounted and create them and delete them as per requirement. The software is playing its role in protecting the contents of mobile devices like laptop disk or removable storage devices via encrypting the whole block devices.
The software comes with a GUI interface working utility with a LUKS-protected file system. LUKS Manager allows users to create, format, and mount the encrypted volumes, and you also have the leverage of having a passphrase USB key or passphrase verifying function. The arbitrary underlying contents of the encrypted block makes the LUKS Manager useful for swap devices encryption. Moreover, the software may be helpful if having specific databases that use mainly formatted block device for the storage of data.
#21 LibreCrypt
LibreCrypt is a reputable disk encryption software for windows that is easy to use and comes with the wizard to create new containers. The exciting explorer mode allows you to access containers in a case when you do not have admin permissions. LibreCrypt is compatible with Linux encryption, such as Dm-crypt, Luks, Cryptoloop, and losetup.
The software is portable and does not need to be installed, but you can find a little trace on 3rd party PCs. LiberCrypt leverage you with support various hash and encryption algorithms in several modes that permit more options than other disk encryption software. Moreover, The software benefits you with the smartcard support and security tokens, and you can use a thumb-drive via having an option for key files.
#22 Gnome Encfs Manager
Gnome Encfs Manager is an intelligent and easy to use software for managing and mounting EncFS stashes that provide key-ring support, a tray menu, and per-stash configuration. The software comes with various unique features and is using the App indicator API. You do not need to worry about the encryption because once the stashes are configured, it transparently works in the background.
The software is designed to work well for you whether you want to mount or unmount your stashes via USB-Disks, network resources, and SD-cards. You can set your preference with multiple options available, and you can either create or import a stash. Gnome EncFs manager is doing the trick with its rock-solid integration into the system and permits to do various things in the background.
#23 SiriKali
SiriKali is an intelligent utility software that effectively manages CryFS, EcryptFS, FscCrypt, EncFS, and SecureFS based on encrypted folders. The software-based on QT/C++ GUI interface and the encrypted folders can freely grow and shrink when the files are added or removed.
You have the benefit of having file-based encrypted containers that are limited to the size, and you can size the box when it is created. The software comes with a graphical user interface that allows users to manage encrypted volumes easily. All the encrypted data is stored at the volume path, and you can use the critical option for password protection.
#24 EncFS
EncFS is an all in one free to use fuse-based cryptographic software that allows you to encrypt files using an arbitrary directory to store encrypted files. There are special permissions required for running and using the Fuse library module to leverage you to have the filesystem interface. EncFS legitimates you to add more translation if the native language is not supported and only partially translated.
The volume key is used to encrypt files that are either stored within or outside the encrypted source directory, and you can use a password to decrypt the key. A significant advantage of using EncFS is that you can work on files at a time rather than an entire block of the device. The software is facilitating the user for data, more importantly, when you are creating a new file system.
#25 CryFS
CryFS is the best in the class cryptographic filesystem for the cloud that encrypts your Dropbox and provides protection against data leaks and hackers. The software is also very efficient with other cloud providers like OneDrive, iCloud, and others. CryFS has a straightforward setup, runs in the background, and your daily workflow will be streamlined in easy access of files. There are two directories, one is used to save the encrypted files, and the other directory is virtual that does not exist.
The software is free to use and comes with many improvements, and is available on GitHub. All your data when leaves from your computer is in encrypted form. Metadata, directory structure, and file contents are entirely secured from the hands of the hacker. CryFS is extremely helpful; if someone steals your hard disk, your data will always remain secure because they cannot decrypt it in any way.
#26 Windows BitLocker
Windows BitLocker is a proprietary encryption program for Windows that encrypts your entire drive. The software leverages to protect against unauthorized changes to your operating system. Windows BitLocker uses the AES encryption algorithm by default in XTS mode, and the key is generated when you have already encrypted your data. You can unlock the data manually using the key.
BitLocker handsomely secures your data via scrambling that requires valid decryption to read it, having a recovered key. The software is entirely different from all the encryption programs because there is a window log in to secure your data, and no extra passwords are required. In case of device failure, you can revert your scrambled data using the key and make it readable again, and your data will remain accessible.
#27 LUKS
LUKS is a software utility for Linux hard disk encryption and is providing a standard on-disk format. The software not only advantages you with compatibility among distributions, but also you have the leverage of secure management of multiple user passwords. LUKS is designed for a secure key setup according to TSK1 and having the same structure as TSK1.
The software stored all the necessary setup information in the partition header that allows you to transfer your data with ease. There are multiple features on offer that are incredibly secure, support for various keys, free to use, effective passphrase revocation, and more to add.
#28 TrueCrypt
TrueCrypt is a leading cross-platform that provides encryption tools that allow you to migrate any encrypted data to virtual disks images on your systems. TrueCrypt offers certain features that create an encrypted container, on the fly encryption of windows, support for hidden volumes, and support for various encryption algorithms and nested double encryption.
The software creates a virtual encrypted disk within a file and encrypting a partition or whole storage device. There are Some unfixed security issues make using TrueCrypt not secure. However, TrueCrypt is automatic, has real-time and transparent encryption, and you have a multi-threaded design scales well on multi-core processors. The software is discontinued for many years, but still, you can use a version 7.1a.
#29 eCryptfs
eCryptfs is an intelligent cryptographic stacked file system for Linux that is POSIX-compliant. The software handsomely stores the cryptographic metadata right in the header of every file to copy the encrypted file between the hosts. The software has a wide usage for the Home Directory encryption of Ubuntu and can be transparently embedded in several network attached storage devices.
There is no need to track any additional information for the files that are already encrypted. The software is adequate and considered to be secured against all known cryptographic attacks. You can use eCrypfs to encrypt partitions and also for the directories that can not use partition regardless of the file system, partition type, and else.