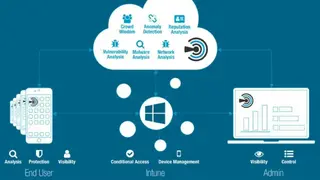
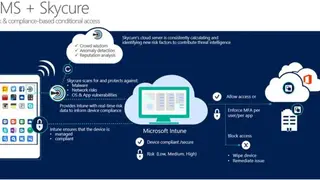
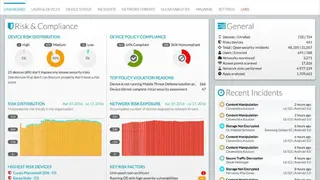
Skycure
Skycure is predictive mobile threat defense services providing the platform that protects against cyber threats and identity theft. The software is helping with its advanced and proactive defense solutions that automatically detect and preventing mobile from cyberattacks by keeping the user information safe and secure.
The software has a complete authorization system and provides protection to many organizations with many network-based threats, malware, vulnerability exploit, and other attacks form both external and internal sources. The software is making its mark with its dual protection procedure that has a client-side module that protects it 24/7, and the server-side permits great lifting analysis.
Skycure has such predictive technology based on mobile intelligence via machine learning and crowd intelligence. The software has a cutting-edge application that is accessibility clickjacking, cookie Stealer, No iOS zone, HRH, linked out that ensure you a perfect solution from future threats. The software is providing enormous benefits to the organization to protect them from any theft and fraud and provide you with in-depth resources to understand about its usability range.
Skycure Alternatives
#1 AVG Internet Security Business Edition
AVG is a security providing software that permits your business to protect against identity theft and fraudulent activity. The software integrates the whole system with security tools that saves all the lethal information that protects your business endpoints against ransomware, malware, hackers, and much more. This software is quick to install and provides 24/7 protection and facilitates you with free e-mail and phone support.
The software lets you save network in real-time with cyber capture, firewall, links scanner, and network antivirus. The cyber capture feature assists you with the un-authorized downloading and firewall protects against online security threats and links scanner that checks the web pages for you before they come into your browser.
AVG is making its mark with identity, data, and transaction protection through anti-spyware, server security, encryption of data, and file shredder. Now you can do remote control and protect hardware via ransomware tool, smart scanner, and remote management tool. The remote management tool allows you to install, update, configure AVG across the entire computer network.
#2 Webroot
Webroot is a cybersecurity and threat intelligence services providing software that provides you the protection against fraud and identity theft. The software comes with all the necessary tools based on advanced technology that permits you to act against cyberbullying. Webroot is assisting too many organizations to save important information, and it secures individuals from cyber threats where they meet.
The software is featuring with its cloud-based solutions from small to large businesses via data privacy tools. Webroot is making quite stunners through providing solutions against viruses for gamers and internet security plus. The software offers many products that are DNS protection, endpoint protection, Carbonite backup for office 365.
Webroot is also serving in-home security by keeping wi-fi data safe and secure and has a complete resource library and in-depth documentation that lets you understand about its usage and tutorials available that you can check anytime. Internet intelligence consists of IP reputation, web classification, and real-time anti-phishing, and the software is also aiding with file reputation, streaming malware detection, and mobile security DSK.
#3 Shibboleth
Shibboleth is the world’s most advanced deployed federated identity solution providing a platform that allows the organization to protect its resources. This software equipped with all the robust tools that let you secure your organization data with no outside access and from any identity theft issues. The software connecting users between and within the organizations and every component of shibboleth are open source and free.
The software is highlighting in-depth documentation that lets you understand about its usage and installation procedure. Shibboleth is featuring many products that are metadata aggregators, embedded service discovery, identity provider, and more. The software aids in single sign-on capabilities and allows many sites to inform about authorization for access in a preserved privacy manner. The software is assisting many organizations with its services that automate the whole identity control.
#4 CAS
Cas is an online customer relationship management service providing software that allows enterprises to grow their business via an enhancement in production. This software comes with a robust integration that automates the whole business process, and it is one of the leading German enterprise’s solutions providing software from small to large size. CAS is benefiting you with profile and history, the board of directories, facts, figures, and data, etc.
The software is providing solutions to relation management, configurator, education, and research. In relationship management, you will find services related to consulting, engineering, information technology, alumni, and much more. This software is giving its services in many sectors that are engineering, commercial, higher education, aviation industry, tourism, associations, and many more to count. This software also has in-depth documentation that permits you to understand about its running procedure.
#5 Connect2id Server
Connect2id server is an all in one open ID connect server for enterprises that based on the open-source network. The software allows you to do single sign-on for web, mobile, and desktop applications with a server permitting you with complete control on consent, authentication, and UX. The software aids with in-depth resources that imparts you with comprehensive knowledge about its usage.
The software lets you operate fully functional openID according to the assurance required by applications and has a federated social, connect attribute, and a partner login sources as well. Connect2id enables you to protect your web sites’ APIs with an access token to prevent identity theft. This software gives monitoring, security, and a 24/7 complete performance in real-time.
Connect2id is making its mark with its advanced services to the customer industries like SaaS, Fintech, retail, media, entertainment, integrators, eGovernment, and eHealth. The software comes with various products that provide you with different services like directory access, authentication for cloud apps, provisioning and synchronizing, web signatures, encryption of the messages, and many more.
#6 LemonLDAP:NG
LemonLDAB is a single web sign in and access management software that permits you a complete management platform for better control of your resources. The software provides three main functions that are authorization, authentications, and accounting. The software offers you with in-depth documentation that lets you understand its running procedure that is easy to maintain and use. LemonLDAP recognized its importance with API integration, web protection, and identity federation services
The software has three fundamental components portal, manager, and handler. The portal service facilitates you with an application menu, CAS, SAML, OpenID Connect, rest Server, and session management. The manager service comes with the function of configuration, notification, and send factors. Lastly, the handler component assists you with access control, custom, and web service token. The CAS function promotes attributes sharing, SAML features let you export and import metadata and discovery protocol, and OpenID connect permits you to authorized codes, implicit, and hybrid flows.
#7 VIPRE Antivirus
VIPRE Antivirus is one of the top-rated antivirus software available on the market that you can use to protect your personal business or commercial company infrastructure from cyber-attacks. To protect your data from malicious attacks and hackers, you need a vigilant digital bodyguard, and this tool serves the purpose perfectly.
The advanced protection offered by VIPRE includes a File shield that guards your computer against viruses, worms, trojans, rootkits, and other threats. It also detects true zero-day threats before they can even take effect, Web shield that keeps you protected against phishing attacks and other online threats, and an Email shield that stops dangerous attachments and links in emails from infecting your device.
Moreover, you also get an Application shield to protect your computer against malicious desktop applications, a System shield for detecting and blocking malicious processes that could cause an infection, a Maintenance shield for Optimization, and a Questionnaire shield for checking if you are running potentially harmful security programs or settings. All in all, VIPRE Antivirus is a great tool that you can consider among its alternatives.
#8 CloudLock for Google Apps
CloudLock for Google Apps lets you move to the cloud faster and with less risk of data breaches. The service solution was acquired by Cisco Umbrella. It makes it easy to allow users to access their Google G Suite from mobile devices and other external networks without ever having to worry about security. The solution is perfect for small businesses that want an easy way to securely access their apps inside their corporate networks or outside of them while also giving end-users permission-based controls over email content. It’s available for all platforms and is compatible with any device. CloudLock for Google Apps is built-in to the popular Google Apps suite of productivity apps, so it’s a seamless experience.
Once you have enabled CloudLock on a device, you can simply use the same app they would have used to access your email or calendar. And because each contact is assigned a unique mobile number, you don’t have to change old habits and just continue to edit messages and schedules as before. The platform also comes with advanced security controls that let you grant or deny certain permissions to individual contacts, so if your company is worried about sensitive data leaking out of the minute details of daily life your users want access for, you’re covered.
You can even link CloudLock to your enterprise’s identity management system to make sure only the right people are able to send mail. Because CloudLock is an API-based cloud access broker, it works with any other secure apps like Salesforce.com and Office 365, as well as any other cloud source like Dropbox or Box. All in all, CloudLock for Google Apps is a great tool that you can consider among its alternatives.
#9 Network Access Control
Network access control offered by Cisco is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. To protect your business assets, you can deploy NAC solutions to detect unauthorized devices connecting to their network. Network operators can implement policies using Cisco’s Network Access Control solution that enforce things like requiring all users to connect through specific uplinks or limit the number of device connections per hour during peak hours. In addition to the data security problem, the propagation of unauthorized wireless devices connected to an enterprise network can also create service management problems.
With increasing numbers of people bringing their own wireless devices into the enterprise, things like locating a specific device or performing software upgrades can become more difficult as well as costly by requiring additional support staff. Cisco’s Network Access Control provides a centralized place for administrators to manage policies related to things like required wireless encryption levels and installation of security software, minimizing the total cost of ownership for managing a network.
By having a centralized point where policies can be rapidly configured and monitored for compliance, administrators can reduce administrative overhead by managing from a single location. It also enforces security policies for wireless connections at the point-to-point port level, and it can be used with or without 802.1x authentication. All in all, Network access control is a great tool that you can consider among its alternatives.
#10 DbProtect
DbProtect is a SaaS platform designed for monitoring and management of enterprise databases, including file systems, applications, and configurations, all from a single user interface. With secure protocols for protection such as firewall rules or intrusion detection, enhanced security features such as encryption or vaulting files for added privacy, plus the industry’s largest database scanning engine with over 350 million database definitions, DbProtect is the ideal cybersecurity solution for organizations seeking to protect their data from attacks.
It also provides the industry’s only full-featured Identity and Access Management system that not only secures endpoints such as desktops and laptops but also mobile devices and network devices, ensuring control is maintained. The solution also enables IAM through a rich user interface, access policies, and macros so that users or administrators can easily and securely restrict even privileged remote access.
DbProtect’s on-demand adaptive firewall architecture means security is maintained without making changes to custom configurations. It offers incident response features such as log scanning and reporting as well as file recovery for those rare instances when data loss occurs. An extensive API is also there that allows third parties to integrate into the platform as needed. All in all, DbProtect is a great tool that you can consider among its alternatives.
#11 Red Canary
Red Canary is a cybersecurity technology company delivering cloud-based security services. It provides complete threat management that includes protection to stop threats before they execute as well as protection for existing malware and ransomware infections. The system deeply understands the behaviors of malware and ransomware; then develops a threat intelligence platform that allows you to see, understand and respond to threats with overwhelming speed.
Red Canary’s Threat Intelligence Platform is a deep-dive into known attacks with a lightweight, fast scan for new threats. It uses machine learning to identify emerging malware and, as quickly as possible, disable them before they cause damage. Moreover, Red Canary’s SaaS technology is used by enterprise security teams to protect themselves from ransomware and other cyber-attacks. All in all, Gluster Cloud Backup is a great tool that you can consider among its alternatives.
#12 McAfee Complete Endpoint Protection
McAfee Complete Endpoint Protection is an elastic, cloud-based security software solution designed to protect you from advanced threats and targeted attacks. It combines endpoint detection and response, encryption and data protection, compliance management, and vulnerability monitoring into a single platform. McAfee Endpoint Protection extends your valuable services and resources with centralized management, consolidated security policies and controls, and simplified administration across multiple endpoints.
This gives you better visibility into your critical assets allowing you to detect issues faster before they become serious problems that threaten data loss or disruption of business processes. It protects you across the endpoint, along with your data center and web infrastructure. Moreover, the solution also provides continuous, bi-directional protection without slowing down IT workloads. And it covers all operating systems desktops, laptops, servers, so there’s no need to worry about windows or Mac OSX compatibility.
McAfee Endpoint Protection also delivers on-premises security and data protection for hybrid clouds. With an array of integrated security capabilities developed to manage those environments, your company focuses its energy on managing a business. All in all, McAfee Complete Endpoint Protection is a great tool that you can consider among its alternatives.
#13 Avira Small Business Security Suite
Avira Small Business Security Suite is an affordable, reliable, and easy-to-use security platform for your business and personal use. Not only does this system offer an easy-to-use interface that both beginners and experts can easily navigate through, but it also offers protection from viruses, spyware, malware. If you need advanced protection with a little more blaze, then Avira Small Business Security Suite is the best option. You have full control at your fingertips from where you can restrict access of employees or guests of your business to keep everyone safe while they’re browsing the internet.
The installer gives you the option of what components you would like to install with your suite. It also allows you to customize the installation by letting you pick which folders will be scanned for threats and how often they will scan them. After a quick setup, a dashboard is displayed with a list of buttons pertaining to the features of your Avira Small Business Security Suite. They’ll display any issues or alerts that have been detected since your last scan, as well as offer information on antivirus protection, firewall protection, online backup, and encryption.
Several options are available for creating rules to configure your firewall settings to meet the needs of your business. A wizard will walk you through configuring different settings, ranging from which programs are allowed to send incoming and outgoing traffic to which traffic can transmit data in both directions. The program allows you to set what applications are able to send out data in addition to being configured with incoming rules. Additionally, it comes equipped with a port scanner that can be used to automatically find vulnerabilities in your system’s protection. All in all, Avira Small Business Security Suite is a great tool that you can consider among its alternatives.
#14 Easy Solutions
Easy solution is a service that provides security systems for the detection and prevention of electronic fraud across devices, channels, and clouds. It is a preventative measure that protects your identity and financial well-being when you least expect it. With Easy Solutions, you can rest assured that every account will be properly monitored 24/7 so you know when something suspicious happens, too much money is paid out in cash, or strange payments are made, which makes you feel uncomfortable about your credit card payments. All in all, Easy Solutions is a great tool that you can consider among its alternatives.
#15 Panda Cloud Protection
Panda Cloud Protection is an antivirus, anti-malware, identity protection, and encryption solution that protect your computer, tablet, or smartphone against all types of viruses, malware, and ransomware. You get real-time protection that blocks any malicious links or emails before they can infect your device. You can also use your device with confidence, knowing that it is well protected.
The program scans for viruses, spyware, Trojans, rootkits, and other harmful programs when they are executed to ensure your data are safe by blocking potential threats even before they are downloaded to your device. It protects against malicious links and downloads, so you can safely browse the web or open attachments without worrying about getting infected or your privacy being compromised.
With this solution, preventing ransomware attacks by blocking malware-encrypted files on an infected computer is so easy. Moreover, you can also get an alert if the apps try to access sensitive information like contacts and location to keep them from stealing your private information. All in all, Panda Cloud Protection is a great tool that you can consider among its alternatives.
#16 Aruba ClearPass
Aruba ClearPass brings agentless visibility and dynamic role-based access control for the enforcement of seamless security and responds to both wired and wireless networks. The strategy that Aruba is using is eliminating the blind spots from where they can begin their work for full-spectrum network visibility. With the help of this, users can get all real-time policies of their devices can connect and what they can access.
It reduces the risks through its Cyber Catalyst to enforce the policy of ClearPass. The solution provides secure Wi-Fi guest access or device onboarding to help the users in connecting their devices to the network to ensure the protection of the network. The solution delivers an efficient way to check the health of laptops that are connecting to networks. It offers a ClearPass OnConnect service that helps the users to secure their Ethernet ports behind their IP desk phones.
#17 OpenAM
OpenAM is open-source software that gives you access management, entitlement, and federation server platform that works intuitively and provides you management and resources integrating facilities for users. It gives you the most advanced identifying tools for digital services and provide you with 24/7 support and maintain, and provide critical security patches.
The program is an open identity platform which gives you multiple sites and application for your business to provide seamless authentication to the various modules. OpenAM offers an authentication module for your customize processes, authorization module for restrict access or desired resource policies integration, identity provider, single sign-on to all services under the system, are some of the most utilized modules of the platform.
The program includes features like high-performance and clusterization extensibility functions. Moreover, it also offers a system development kit. It also comes with a security module that closes all the possible vulnerabilities and does multiple tests to ensure an effective security protocol. It also helps in solving the issue on your platform.a
OpenAM has an excellent interface and provided services on a cloud-based platform and gives dedicated software for various operating systems. Then the direction feature works beautifully, and it comes with the free trial version of 30 days.
#18 SimpleSAMLphp
SimpleSAMLphp is a leading PHP frame-work authentication services providing the platform that assists with a large number of external contributors. The software provides you with the identity protocols and frame-works like shibboleth, CAS, OpenID, and WS-federation and is easily extendable that permits you to create your modules. The software comes with a guide library that provides you with information if the installation is not successful.
The software provides you with the security advisories that give you situational solutions to save the system from the internal damage. Many security advisories are log injection, reflected cross-site scripting, authentication context bypass, link rejection, and more. The platform facilitates you with the third-party modules, and different themes provide you with the customization option to change the look of the page.
#19 Gluster Cloud Backup
Gluster Cloud Backup is an open-source software scalable, network filesystem that can be used to produce caching servers, NAS devices, or scale-out cloud storage servers. Its Cloud Backup makes use of GlusterFS, an open-source filesystem. The system is designed for reliable backups using the principles of erasure coding. It allows for scalability of capacity and performance. This makes it an ideal type of system to use in the cloud. The software itself runs on commodity hardware that can run on almost any operating system platform.
Gluster Cloud Backup provides automated backups with proper retention policies built-in; this prevents you from having to manually manage files or keep track of them which can be difficult with some methods. You can deploy this in a cluster of distributed nodes, allowing scalable data throughput and storage capacity. The distributed nature also allows for multiple administrators to manage different sections of the cloud backup system. Gluster Cloud Backup can be used to create multi-protocol access for files.
The software uses its own FUSE plugin to allow you to mount the cloud backup system through many other applications, such as Samba, NFS, FTP, Rsync, etc. With Gluster Cloud Backup, you can use an external storage device or NAS system to store your backups. This allows you to keep your work files on locally attached drives or in a remote server while keeping your backups in the cloud. Because of the distributed nature of the software, it is possible for multiple workstations/servers to operate at once without overwhelming the network. All in all, Gluster Cloud Backup is a great tool that you can consider among its alternatives.