Trend Micro Apex One
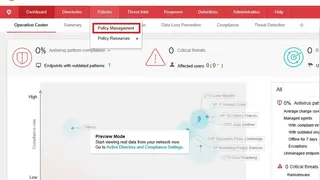
Trend Micro Apex One is intelligent endpoint protection and security platform that delivers real preventative security out of the box. Installed on the endpoint, it blocks threats invisible to legacy solutions and quarantines threats that other solutions allow through. These capabilities provide you with a proactive next-gen security solution that is faster, smarter, and more efficient than ever before. The solution combines advanced threat protection that stops known and unknown threats with zero-day exploit defenses that block attacks that other platforms allow through.
Trend Micro Apex One also integrates seamlessly with your network security systems to provide real-time threat intelligence from your cloud endpoint so organizations can achieve faster incident detection with faster detection and response times. Its multi-functional agentless design integrates everything IT needs to secure their endpoints in one platform: cloud-based threat intelligence, real-time prevention, simple installation, management, and reporting.
Trend Micro Apex One Alternatives
#1 NetWitness Network
NetWitness Network is a next-generation intelligent threat detection and response solution that leverages big data and cloud technologies to help organizations detect and investigate potential cyber threats before it’s too late. It Features Device Detection and Malware Analysis, File Analysis (PCAP Files, Malware, and File Reputation), Endpoint Analysis, Endpoint Detection and Response, Endpoint Control and Compliance, APT1 Analysis, Digital Footprints, Threats, Malware, TTP, and Geo-Location. Use its eDiscovery module to easily manage the security review process and reduce time to detection by aggregating, classifying, and analyzing billions of events per day across your network.
Capture data continuously so you always have it for your next investigation or incident response. Moreover, you can automate various processes with custom searches and queries and integrate them into any existing SIEM for active monitoring and data collection. The result is a threat detection platform that uses big data analytics to predict and mitigate cyber threats, providing the speed and accuracy needed to protect sensitive data and ensure business continuity.
#2 Qualys Cloud Platform
Qualys Cloud Platform is a data security and compliance platform that provides a complete security and compliance solution for organizations of all sizes, from large and global enterprises to small businesses. It serves as a centralized portal for the discovery, monitoring, and security testing of all cloud applications in use by an organization. The system also offers a data breach detection alerting feature that enables an organization to detect in real-time when just one user is impacted by a data breach.
The platform reduces complexity by offering integrated vulnerability management, configuration, and compliance management all in one place. And that eliminates the need to acquire, configure, deploy and manage multiple tools. Built on an elastic, secure, scalable cloud platform, Qualys Cloud Platform is built for continuous compliance. Discover exposed data across diverse infrastructure and endpoints, so you can take proactive steps to protect your assets.
#3 Rapid7 InsightIDR
Rapid7 InsightIDR is an incident detection and response solution combining multiple advanced security software capabilities in a single platform. It provides true visibility into the endpoints and applications running across the enterprise in real-time. Key features include seamless integration with multiple popular vulnerability assessment tools, Threat intelligence updates from leading sources, Endpoint monitoring, including a behavioral analysis of key system processes, and an extensive collection of comprehensive false positive mitigation data. The solution is designed for organizations that require a single platform to identify and respond to advanced threats, both internal and external.
With built-in domain knowledge and graph database technology, InsightIDR automatically maps IP addresses to domain names and records, including all subdomains, and identifies the associated companies for easy mapping across the organization. This feature can resolve incidents with ease, even in large-scale environments. Using threat intelligence feeds, it can quickly tell whether domains were registered by a potentially malicious actor and which domains were involved in an attack.
#4 PURVEYOR
PURVEYOR is an artificial intelligence-based cyber defense platform that enables organizations to protect themselves from cyber-attacks before they can affect their business. With this solution, you will be able to detect security threats faster and thus react appropriately in a timely manner. The platform integrates all of your threat intelligence, automated response, and incident detection/response capabilities into a single, easy-to-use tool.
Its unique technology enables users to keep up with the rapidly increasing volume of threats and constantly changing cyber-threat landscape by automatically applying the right action to each security event based on the threat intelligence they’ve gathered. By offering the first and only comprehensive solution in the market, PURVEYOR is able to significantly reduce the time it takes to respond to and detect a cyberattack while lowering both the cost and risk associated with responding.
#5 Securonix Security Operations and Analytics
Securonix Security Operations and Analytics cloud-based platform provide teams with real-time visibility, context, and analytics across the most critical security controls to minimize risk and accelerate investigations. Frontline teams can now investigate threat events and create new alerts instantly. The solution features a unique ‘record, review, respond’ approach that enables frontline analysts to use visual intelligence to investigate new alerts or follow up on potential incidents.
It leverages advanced machine learning and behavior analytics to reduce false positives and give you a complete understanding of user and entity threats. Even with behavioral analytics, it is difficult to find abnormal user behavior. Many users and entities have multiple accounts and may work on different networks. Securonix gives you the ability to track users across accounts and trace lateral movement and nefarious activity. All in all, Securonix Security Operations and Analytics is a great solution that you can consider among its alternatives.
#6 Stellar Cyber
Stellar Cyber is a cyber-attack detection and response platform that protect enterprises against the latest cyber threats, such as Ransomware, Cryptojacking, Banking Trojans, and Multi-Stage Attacks. It provides an automated and dynamic sandbox environment, enabling quick delivery of response services that include protection against a wide array of threats. With cyber threats becoming more sophisticated and prevalent by the day, enterprises need to keep their network security in check.
By combining advanced threat intelligence with threat analysis, Stellar Cyber monitors thousands of endpoints across your network in real-time, detecting and mitigating advanced threats at their earliest stage. It actively searches the internet and dark web for new threats that target your company and alert you before it’s too late. Moreover, the software helps keep data physically resident in a specific site or region to prevent sensitive data from moving across borders. All in all, Stellar Cyber is a great solution that you can consider among its alternatives.
#7 Cybrhawk SIEM ZTR
Cybrhawk SIEM ZTR is an AI-based cyber security information and management software that allows companies to manage all cybersecurity-related tasks, reactions, and processes in one place. It provides companies with full visibility into all cyber-attacks, threats, and vulnerabilities. This advanced tool facilitates corporate IT and enhances the overall performance of the cyber defense in the enterprise. Moreover, Cybrhawk SIEM ZTR is a fully automated platform that delivers advanced technology that monitors, assesses, and protects the cybersecurity status of your enterprise.
By using this cutting-edge system, you can protect your company data by detecting potential risks and threats in real-time, augmenting your business profile against cyber-attacks, and managing your entire computer system with ease. With this solution, enterprises can now focus on their core business goals and trust their IT department to focus on cyber security. The solution is integrated into a single dashboard that is seamlessly connected to all enterprise systems and infrastructure and reduces the manual effort required for cyber security incidents.
With this artificial intelligence-based technology, the SIEM ZTR automatically identifies and prioritizes security incidents and takes immediate actions to mitigate threats, helping enterprises prevent and recover from attacks without human intervention.
#8 Cysiv
Cysiv is a comprehensive cyber security platform that provides a single, centralized solution for all security needs. You can scan and fix known vulnerabilities in your devices, computers, and network. It comes with powerful signature-based threat protection and blocks any new kind of malware before it reaches your devices or networks. Whether it’s phishing scams, fake websites, malicious links, or infected or unwanted software, Cysiv protects you from the potential dangers on the internet. With data analytics and a real-time, user-friendly interface, the solution provides key insights into cyber threats and assesses the overall security posture of an organization to inform decision-making.
The patented, cloud-based platform provides comprehensive threat protection across the enterprise, including on-premise data centers, servers, and laptops. Unlike other solutions that focus on only one of these dimensions, Cysiv’s unique approach identifies threats that already exist inside your network and lets you automatically share information with IT peers or third parties outside the organization.
#9 Syxsense Secure
Syxsense Secure is an endpoint security management solution that makes it easy to manage your endpoints and associated security risks. Targeted to corporate IT professionals, the solution provides a comprehensive view of your organization’s endpoints, allowing you to keep track of vulnerabilities and security settings across your entire network. This platform is necessary to combat the increasing volume of threats posed by data leaks and phishing attempts that help cybercriminals gain a foothold in your network. With Syxsense Secure, you can see what’s happening on your endpoints and then react and respond to the threats with confidence.
The enhanced Anti-Virus adds new layers of protection to known threats for complete endpoint protection. Features include real-time and cloud-based protection, procedural change control, vulnerability protection, and more. All these features keep sensitive information on company devices from falling into the wrong hands and prevent access to unauthorized websites, ensuring productive work time and protecting your users from outside threats.
#10 ThreatDefence
ThreatDefence is a managed threat detection and response platform that can detect and respond to attacks from brute-force attacks to automated tools to social engineering and email phishing. Using its controls panel, you can test your security to see how well you’re responding to threats. It provides real-time monitoring for automated threat detection and is built on the principles of best-in-class technology, expert-driven security, and effective incident response. ThreatDefence provides a suite of features that enable customers to track attacks, evaluate risk, and respond accurately to threats.
Its Deep Visibility feature works seamlessly with existing technology, eliminating blind spots and enabling true end-to-end detection and response capabilities. ThreatDefence’s Adaptive XDR platform embraces all your security data from any environment: cloud, SaaS, network, on-premise, remote, or virtual. It collects more security events than any other vendor, correlating events from various attack surfaces and revealing even the most covert malicious activities.
#11 DNIF
DNIF is a cloud-based data security analytics platform designed to proactively detect and combat advanced cyber threats. Its patented technology provides the first truly automated threat feed and security analytics software solution that leverages the power of Big Data and machine learning. The platform’s Auto-Sentry AI software engine automatically and continuously analyzes hundreds of millions of records in real-time for potential cyber threat indicators.
This is performed without the need for manual configuration or tuning, providing security teams with instant insights and threat intelligence to help them keep pace with ever-evolving cyber threats. By analyzing massive volumes of streaming data, DNIF has developed proprietary algorithms that leverage unstructured data residing in unstructured systems such as endpoints and email servers, where 90 percent of the data related to attacks resides.
By doing this, the platform provides users with a continuous stream of real-time insights into threats, rather than relying on isolated security events, giving security teams the ability to identify and respond to cyber threats before they become major breaches. Moreover, DNIF has the capability of providing real-time data analysis using advanced analytics techniques to help detect malicious insiders, events, and activities, enabling organizations to take corrective actions earlier in the attack lifecycle.
#12 SecBI XDR
SecBI XDR, now acquired by LogPoint, is a powerful, highly scalable detection and correlation engine for security events across hybrid IT that can easily collect, enrich, store, analyze, monitor, search and alert on a log, event, and packet data for cyber security and insider threat detection. It provides customers with a unified solution for real-time threat detection, response, and continuous monitoring of their environment in a single console. While many solutions exist to investigate alerts in your network or processes, none exist to investigate alerts outside your organization, in the cloud, or on external websites.
LogPoint allows you to take better control of your security posture while increasing your overall security results and lowering your security incident response time. The solution can be deployed in minutes on a virtual machine or as an appliance at any scale, with free support for up to 500 events per second and up to 200,000 events per day. The solution transforms the information security landscape by providing organizations with extended capabilities of SIEM through the use of 3rd party log sources alongside traditional log sources.
#13 ReaQta
ReaQta is a technology company that provides security and threat management solutions for endpoint devices, IT environments, and cloud services. It offers real-time detection of any application that tries to make a change to the system and provides an instant alert if something suspicious is detected. It combines agentless application control, cloud-based vulnerability assessment, web application control, and advanced threat protection to protect enterprises from advanced threats, data breaches, and data exfiltration.
It protects your endpoint and data from cyber-attacks by monitoring for malicious, anomalous, and suspicious activities, analyzing the behavior of applications, providing alerts and notifications, and blocking rogue applications. You can quickly identify breaches and prevent or contain data leaks by generating comprehensive forensic reports which can be easily shared with your customers and partners. All in all, ReaQta is a great platform that you can consider among its alternatives.
#14 Gurucul
Gurucul is a cyber security and risk analytics platform that allows companies to see beyond their firewalls, patching, and antimalware solutions. Organizations can visualize the threat landscape of their organization in one view, analyze the effectiveness of their security posture and identify vulnerable endpoints. It gives you a single user interface to manage both Security and Risk and project a higher ROI on Security Investments. It gives organizations real-time visibility over all their data sources and helps them to assess the value of their data, exposures to risk, and compliance.
Gurucul’s technology leverages Big Data and Artificial Intelligence to uncover hidden connections in data, providing the most accurate and insightful information available. Reduce the threat of data breaches and compliance exposure with a proactive response to threats and improve the security of your customers through education on threat vectors, security best practices, and real-life case studies of attacks on businesses similar to theirs.
#15 SecurityHQ
SecurityHQ is a cloud-based managed security service platform that empowers organizations with the tools they need to detect and prevent cyber-attacks, protect their assets and identities, and respond to incidents when they do occur. The platform delivers a holistic approach to security, giving CISOs a holistic view of their companies’ vulnerabilities and risks. This approach is delivered through a combination of vulnerability management, network security monitoring, web application monitoring, user behavior analytics, and remediation services.
SecurityHQ offers a suite of modules that are configured to work together to keep endpoints and data safe. The Security Modules can be either deployed on-premise, in the cloud, or both. It also offers advanced backup and disaster recovery services. Rapidly identify and limit the impact of security threats and risks with 24/7 threat monitoring, detection, and targeted response. All this is done by real-time log analytics, with security orchestration, automation & response tooling for investigation, threat hunting, and response.
#16 EventTracker
EventTracker, now rebranded to Netsurion, is an enterprise-grade managed network security and compliance solution that help companies eliminate security risks, increase productivity, ensure compliance, and gain a competitive advantage. Its products and services include a managed firewall service, wireless and internet security, secure access products, and secure connectivity products. It helps companies keep their network safe and secure by handling the deployment and management of your networks. The solution address a range of security issues, including phishing attacks, mobile device threats, ransomware attacks, malicious software like viruses and worms, and more.
It allows you to monitor your entire network and receive real-time alerts about significant changes. You can also set up custom rules for services on your network, such as if a server goes down or the temperature of a server rises beyond safe levels. Moreover, Netsurion’s patented management of technology makes it easy to quickly and effectively deploy, monitor, and manage multiple managed security providers from one portal.
#17 Cynet 360
Cynet 360 is a cloud-based XDR, Response Automation, and MDR platform that allows you to create a unified front-end for your security operations and incident response teams. It gathers data from multiple data sources and unifies the information into a single interface for analysts to investigate alerts and investigate security incidents. It provides unlimited scalability and visibility into all aspects of the threat lifecycle, including malware, phishing, and compromised websites, and can mitigate this fraudulent traffic before it impacts the organization.
The platform works on principles such as machine learning to detect and mitigate phishing attacks, ransomware, and malware attacks. Cynet 360 automatically blocks the malware via an automatic response mechanism and educates users on the malicious links so they can be protected in the future. The machine learning-based rules are continuously updated automatically. Moreover, it provides advanced data protection by encrypting the data, making it inaccessible to the hacker. It also offers report generation, an API for integration with existing solutions, and custom threat feeds for compliance and risk management.
#18 XcellSecure Vulnerability Management
XcellSecure is a futuristic platform that comes with the exclusive management of vulnerabilities. It offers a vast range of manual tests closely assigned with multiple methodologies, including the OWASP. You can collaboratively work with your team members to understand and fix any issue. It provides the most careful scoping of the test environment to establish the testing exercise’s exact extent. This platform offers Managed VM that exclusively manages all risks and free up security initiatives.
XcellSecure Vulnerability Management supports the best level of security that every organization demands. The advanced system comes with security patches, modified end-user policies, upgraded infrastructure, and more valuable services. For authentic online payments, it integrates with multiple online payment apps like PayPal, Maestro, Master Card, VISA, etc. It provides an access-control approach for various devices connected to company networks. Moreover, it offers the best technical account manager, salable cloud solution, integration, correlation, remediation policies, assignments, protective cloud data, SMB cloud, supportive teams, and many more.
#19 Tenable.io
Tenable.io is a versatile platform that comes with the solution of fixing vulnerabilities for lowering harmful risks. It provides a realistic view of all assets by advanced scanning, active agents, cloud connectors, passive monitoring, and CMDB integrations. You can easily and quickly gather vulnerability data, data science, and threat intelligence for detecting and fixing risks. It exclusively covers more than sixty-two thousand vulnerabilities with the complete security and CVE configuration.
Tenable.io continuously assesses and tracks all assets and their vulnerabilities, even the IT assets like virtual machines, cloud instances, containers, and mobile devices. The advanced and progressive dashboard provides immediate insights and reports for rapid analysis and critical issues. Moreover, the advanced-based system enables to management and visualize OT risks from any place. For any query or problem, you can directly contact skilled support teams.
#20 BreachLock
BreachLock is a versatile platform that provides scalable and smooth penetration testing services for vulnerabilities. The SaaS-based platform gives a quick penetration test with authentic offline and online reports with a single click. The advanced platform offers dynamic scaling services both by network and application. You can be facilitated through the best DevOps security testing that meets all your needs. Moreover, it offers you complete access to security team experts to which you can ask you’re desired queries and requirements.
BreachLock continuously scans all the tests for in-depth facilitation and security. It offers web scanning with unlimited access to certified security searchers through a single click. You can directly connect the skilled and professional support teams for any guidelines and queries. It also allows you to inform them about your scope or ideas without any hassle. There is also a comprehensive service of penetration testing through Cloud with more accuracy and quickly. More features can create tickets per finding, updated retest report, business logic testing, onboarding instructions, etc.
#21 Digital Defense
Digital Defense is a best-in-class SaaS-based platform that offers complete security for threats, vulnerabilities, and complexity. It automatically detects and fixes multiple threats and problems before their effect on the network. You can instantly get authentic reports on all the issues and vulnerabilities. It is an innovative and easy-to-use platform that quickly tests hundreds of assets on one subscription. Moreover, it provides the best cybersecurity services for all your information structure and data without any difficulty. The always active online user support deals with all your queries and gives expert guidance.
Digital Defense has a scalable multi-tenant architecture that offers complete real-time scanning according to your desire. It helps to get maximum business profit with the leading vulnerability management technology. This platform offers more features, including low initial costs, user-friendly operation, comprehensive support, traini9ng, professional services, security automation, peer comparison, ROI, rapid monetization, etc.
#22 Qualys
Qualys is a leading platform that offers cloud security, compliance, and related services founded in 1999. The cloud solutions and their integrated application help businesses simplify all kinds of security operations and lower the cost of compliance by providing critical security intelligence on demand, automating the full spectrum of auditing compliance, and protecting IT systems and web applications.
It is the first company to deliver an on-demand solution for security risk and compliance management. The platform monitor your company’s vulnerability management process tracks remediation, and ensures policy compliance.
Qualys’s Guard has also deployed security on-demand platforms in the world, performing more than 150 million IP audits per year with no software to install and maintain. It is a simple yet powerful security solution that comes with a powerful dashboard where you can easily access all features, track threats, analyze data, generate reports, etc. It also has a list of a core feature that makes it better than others.
#23 Rapid7
Rapid7 is a platform that provides services in the field of analytics and security data solutions that enables the organizations to move forward with an analytics-driven approach to cybersecurity. The platform helps the companies by reducing risk across their entire connected environment. It offers diverse solutions, such as assisting in managing vulnerabilities and investigating attacks.
The software provides managed application security by offloading the user’s application security program from scan management to penetration testing. Moreover, it also provides 24/7 monitoring services to defend against threats and prevents attackers from attacking.
Rapid7 offers to design and to implement InsightCinnect Workflows to enable orchestration and automation of the company’s tasks. Other vital features are User Behavior Analytics, Endpoint Detection and Visibility, Visual Investigation Timeline, Deception Technology, Live Dashboard, and Container Security. Lastly, it analyzes all the areas which are vulnerable to risk and expands its security influence to all these areas.
#24 AlertLogic
AlertLogic is a well-designed security software that works as a security guard for your business. This platform connects multiple elements, just like intelligence and experts, to facilitate you with extraordinary secureness and peace of mind for your business.
If you are facing multiple issues regarding your business security or you think that your business is not in a safe hand, then connect to AlertLogic. It is a powerful security solution that comes with all the leading tools and features. Due to a stronghold on your data, it doesn’t allow any unauthorized person to break into your data.
Alertlogic is used widely and provides 24/7 network security to your business. Installing and purchasing this software is much easy; all you need to connect with the organization through their official website. It will provide you with several packages, and you can select any one of them according to your needs. The organization will also help you regarding the configuration process.
#25 Tripwire
Tripwire is an all in one cybersecurity and compliance solutions providing a platform that maintains the needs of the enterprise and organization with the security tools. The platform is doing businesses to remain one step ahead via overcoming all the cyberattacks, and you have advanced cybersecurity controls to take all the security concerns out of the way.
Tripwire is the way to go in identifying the things that are vulnerable in your department and make configuration accordingly. The platform brings real-time change intelligence that will change the whole scenario for you to detect the threats that are extremely high risks. Tripwire is featuring support with IP360 that is allowing you to take things into notice who is in your network or not.
Moreover, you have an extensive log center that will support the collection of data in a secure and reliable way, and you can customize your collection and filtering rules using a Visio-like drop and drop interface. Furthermore, Tripwire is a definite option for you and is maintaining all the compliance needs of the industry, having a best in class automated regulatory compliance.
#26 Whitehat security
Whitehat security is a renowned security software that protects your business in multiple ways. It protects the critical data, manages the risk, and ensure compliance. This platform is designed exceptionally through which you don’t need to have in-depth understanding; you can use it without facing any problem.
This platform combines artificial intelligence technologies, human intelligence, and automation that makes it unique as compared to the other security software. This platform also includes a scanning tool that scans the whole database to find and eliminate the threats from your system.
After installing this software, you can easily access it’s all tools and features. There is also has a 24/7 support feature that helps you if you faced any problem and will provide you with the best solution for your issue. Whitehat security is a choice of multiple international organizations, and it has a five-star review rating on the internet.
#27 Armor Anywhere
Armor Anywhere is a high-level SECaaS platform. It reinforces and binds together your on-premise, open, private, and crossbreed cloud situations. The software comes with advanced security tools to deliver complete security by dealing with the everyday issues of running a cybersecurity group and all the innovation and instruments.
It is known as a leader in data security that provides organization data security without the additional headcount or burden to your IT team. With this, not only will your organization save time with its streamlined cybersecurity solution, but you are also free from the complexity of bringing in a security operations task force.
One of the best facts about this security solution is that it is perfect for Amazon Web Services that protect your data from any threats. It is also known as a security manager that automates all the security tasks. Armor Anywhere offers multiple price plans and each plan has its own cost.
#28 Ciphercloud
Ciphercloud is an organization that provides a platform of cloud access security broker. On this platform, you will get multiple protection services through which you can keep your company’s cloud-based applications safe. Ciphercloud also includes numerous security technologies that allow you to manage or control the encryption keys.
It also provides you a facility to encrypt data on the smartphone, and the best thing is that only authorized persons can access that data. Ciphercloud provides high-level encryption of your cloud data. If your company has strict data residency requirements, then don’t need to worry because this software replaces sensitive data with multiple unique identification symbols that you can use with cloud apps.
It will also keep you update with the threats and other reports of your system. In case of any danger occurs, Ciphercloud will start notifying you and block threats. Due to the robust scanning system, this software scans your whole data accurately. It is commercial software and offers multiple price plans. Each plan has its own cost and features.
#29 Cloudsoc
Cloudsoc is a software that provides the safest platform for your business to confidently run multiple services and cloud applications without facing any thread. It helps you out to detect and eliminate the thread and also keeps you notify whenever you are going to perform any risky activity.
In case if you have performed a risky activity, Cloudsoc will provide a high-level of security that will keep you safe from the threat exposure. Indeed, every business has some private and sensitive data; a small mistake can result in a loss or stealing of the data.
To keep your data safe and secure, Cloudsoc facilitates you with extraordinary protection that will not allow any unknown person to steal your data. You can also make a backup of data through this software. Except for all of these features, Cloudsoc also keeps your different software safe from the approach of a data thief.
#30 AVDS
AVDS is a successful management and vulnerability assessment software that delivers very accurate reports that you can use with full confidence at multiple places. This software includes numerous factors that make strong network security and keeps your network safe by eliminating the vulnerabilities from it.
It is specially designed to scan networks from 64 to 200K active IPs and provides a simple interface or user console on which you can easily manage the various task within a few clicks. AVDS detects the threats in three cases to deliver complete security.
Firstly, when the operating system coded poorly, and that allows an unauthorized person to enter your network. Secondly, when your system software is affected by the different viruses and in last, when the whole system misconfigured. It is effortless to install AVDS in your PC, and it doesn’t require any external software agent. AVDS works very fast to figure and eliminate the vulnerabilities of the network.
#31 Zscaler
Zscaler (Zscaler Cloud Platform) is a high-security application that keeps your internet traffic and access to internal apps safe. It doesn’t matter from where you are accessing the internet, Zscaler will always keep your browsing secure from the unusual threads. It comes with some new protection features that save you from all kinds of malware attacks.
With the help of the Zscaler private access feature, you can safely access your company’s internal resources from any spot. This software also notifies you whether you are connected to the safe network or not. Not only this, but it also recognizes when you connect to the Wi-Fi hotspots where you have to accept use policy before getting connected.
Zscaler automatically disables its services for a small passage of time, and after that, it gets re-enable. It is straightforward to use this app with various accounts, but you have to log out each time. Due to the high security, the app can demand to re-enter the password that is set by the organization’s admin.
#32 Threat Stack
Threat Stack is a computer security software that provides cloud security management and compliance solutions to various businesses using the SaaS model. It is an advanced level solution that gives eternal security checking in cloud conditions to arrange and controls security.
Threat Stack is also known as an autonomous stage arrangement planned for organizations of all sizes working on-premise or in broad daylight, private, or crossbreed cloud situations. Danger Stack expects to wipe out the requirement for numerous point arrangements in the cloud and gives clients a single view into the outstanding coordinated task at hand experiences, framework checking, powerlessness the board, risk insight, and consistently revealing.
It permits clients to make their standards and channels to all successful screen occasions explicit to the necessities of their organization, association, or condition. Threat Stack offers a dashboard where you can access and control all functions.
#33 CloudPassage Halo
CloudPassage Halo is a network security providing platform that delivers continuous compliance, protection, and comprehensive visibility to reduce the risk of cybersecurity. It takes out vulnerable sides and permits you to recover security control over the entirety of your records, memberships, districts, administrations, and assets.
Rapidly find and stock resources being used over any number of open cloud conditions being used in your association to all oversee digital security hazards. It also decreases the attackable surface zone of your open cloud arrangements via consequently and consistently recognizing the most serious dangers and most defenseless administrations with CloudPassage Halo.
Rapidly locate the most basic vulnerabilities, misconfigurations, and changes in your open cloud situations that open your association to digital dangers. Empower quick and powerful occurrence remediation by giving noteworthy data to the individuals who need it in a computerized manner using Amazon SNS and other notice systems. CloudPassage Halo clarifies how your security program is affecting by recognizing to what extent issues have existed in your condition.
#34 Adallom
Adallom is a cloud security software that delivers visibility, governance, and protection for cloud applications. It also secures the audits user activity, usage of SaaS applications, and protects digital items and employees from the real-time threats. The solution contains all useful tools used to build consistent security within the enterprise.
Adallom is quite simple to set up, seamless to users, and is available as a SaaS-based or on-premise solution. With the help of this, you can easily protect your data in the cloud. It comes with several security tools and features that automatically block threats. Adallom is commercial software and offers multiple price plans, and each plan has its own cost and benefits.
#35 Netskope
Netskope is a software that helps organizations to protect their data from various threats in cloud infrastructure, web, and different cloud applications. Its programming conveyed as a SaaS through a disseminated cloud in SOC-2 server farms. The arrangement steers cloud and Web traffic to a cloud-local help for the motivations behind review and strategy authorization.
Customers of Netskope sign into the product using an internet browser interface where they can get to examination on the cloud, cloud use, and set arrangements to control and verify explicit use conduct or caution an overseer. Netskope offers diverse organization choices for traffic directing for examination and approach control.
These include log ingestion, API connectors, a specialist less forward intermediary, turn around intermediary, slight operator, and profile for remote clients on PCs or cell phones, and GRE and IPSEC burrowing. Netskope can authorize strategies including information misfortune anticipation (DLP), against malware, encryption, get to control, and episode the executives benefits on the cloud and web traffic it examines.
#36 Bluecoat
Bluecoat is a cloud-security solution that scans the complete cloud and identifies potential vulnerabilities. With the help of this software, you can find threats and neutralizes. The software also blocks malicious programs based on whitelisting of apps and static code analysis. Due to security analytics capability, each information is recorded and indexed so that threats cloud be identified.
Bluecoat is a complete computer and cloud security program that includes features such as anti-spam, email attachment protection, intrusion detection system, web threat management, and web traffic report, etc. Each feature on this software uniquely created and test by an expert team to deliver complete and stratified experience. Bluecoat is commercial software, and you can use it on Cloud, Windows, Android, and iOS devices.